春秋杯冬季赛2025
本文最后更新于 2025年1月19日 晚上
Web
easy_flask
模板注入无waf
1 | |
或者fenjing也可以
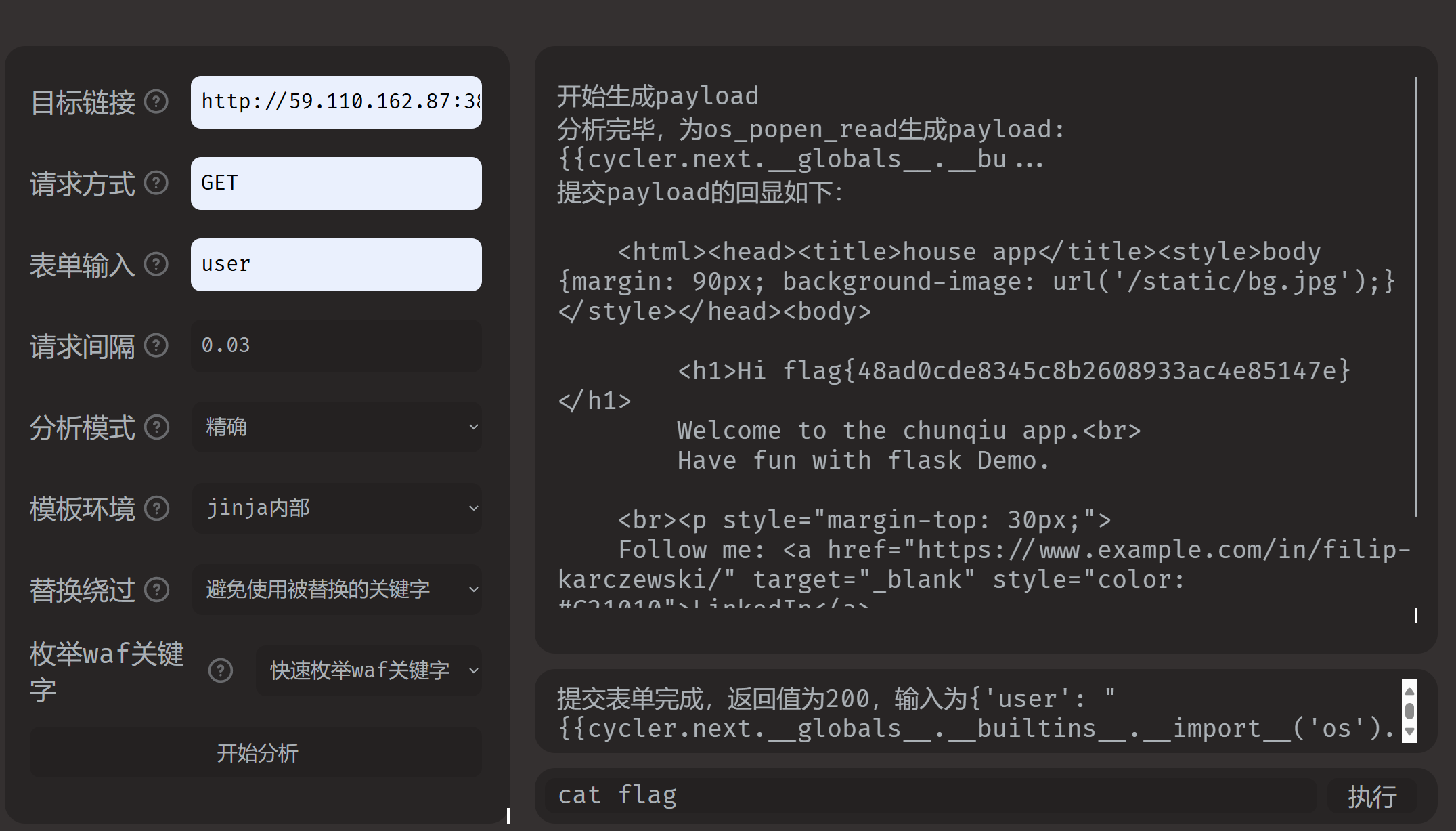
file_copy
yakit抓包尝试报错看到用的是copy函数,filter的漏洞利用
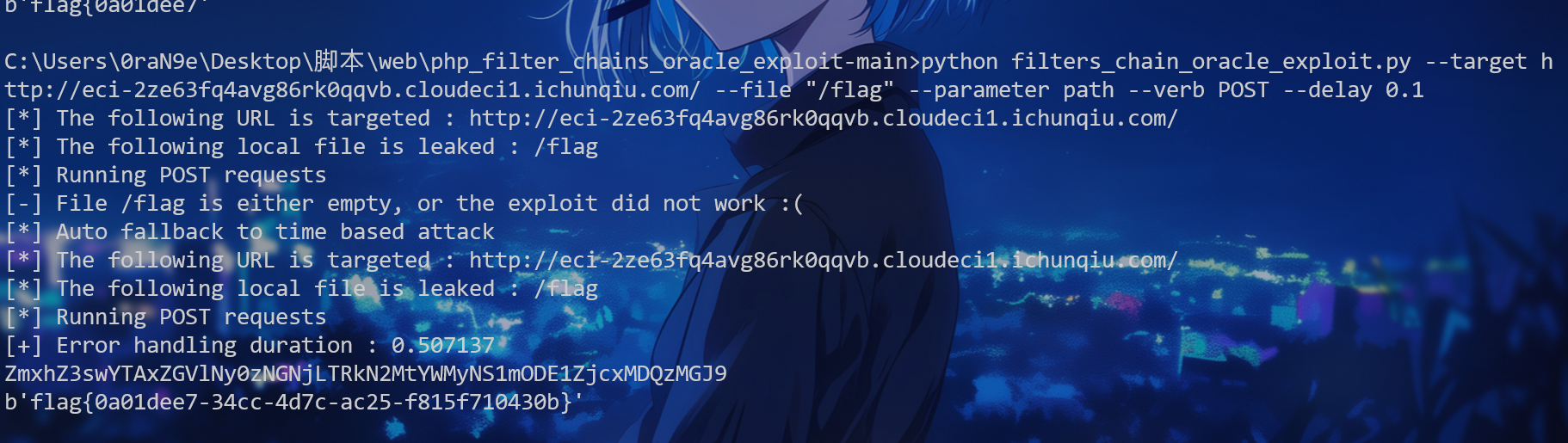
gotar
分析一下源码,想到了软链接,通过指向得到flag
tar软链接读取
1 | |
访问
/assets/extracted/flag
easy_ser
1 | |
b0okshelf(浮现)
首先dirsearch扫一下,有backup.zip,代码主要看update.php和data.php
1 | |
可以写入内容,有字符串逃逸,看一下给的info内容
1 | |
1 | |
传入summary,然后给content写入🐎可以拿到shell,不会了,就到这吧。
easy_php
原题并且有非预期
1 | |
easy_code
在gogogo.php里有内容
1 | |
%0a绕过第二层,第三层用科学计数法,cookie:pass=admin
最后filter去往上找找相关的替换一下就行
crypto
你是小哈斯?
1 | |
通往哈希的旅程
hashcat爆破
funny_rsa
1 | |
Misc
简单算术
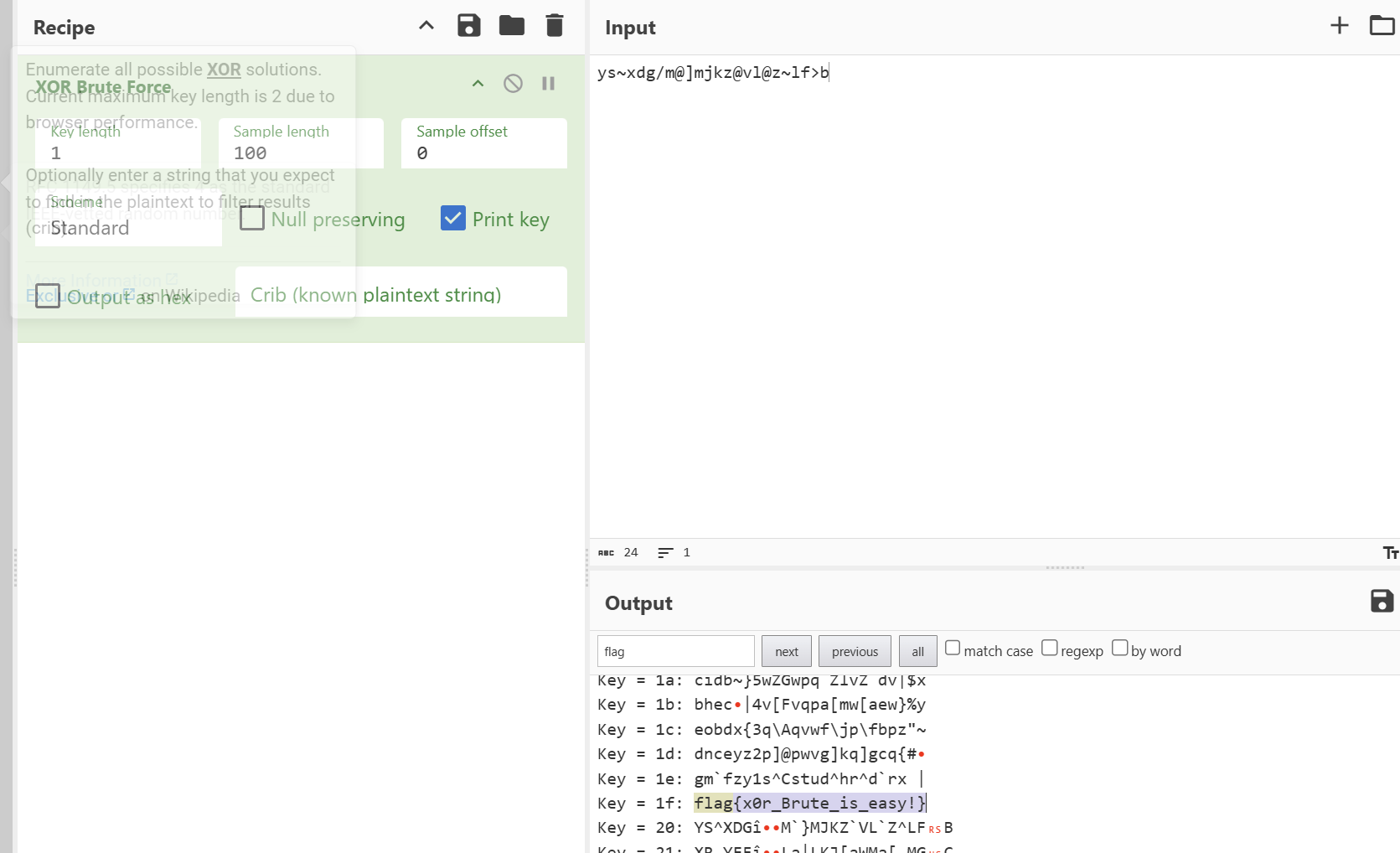
压力大,写个脚本吧
1 | |
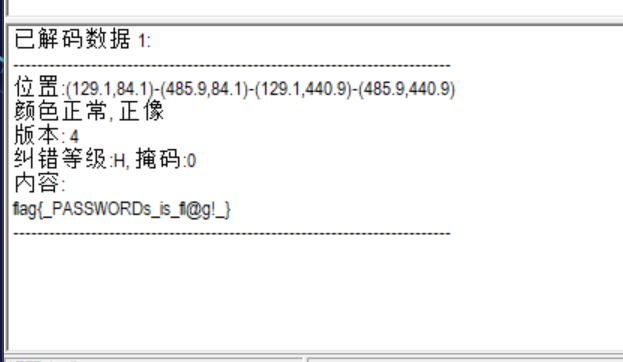
得到二维码,扫一下得到flag
See anything in these pics?
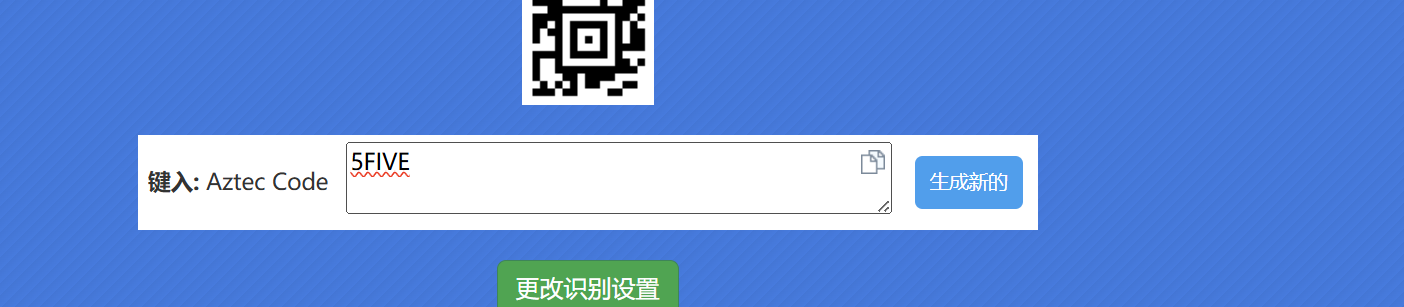
然后010搜索到8950,提取改宽高

Weevil’s Whisper
定位一下shell1.php的源码,是个php混淆,解密一下找到最后一条流量放入解密。
1 | |
音频的秘密
wav的deepsound的密码弱密码,答案是123,然后进行bkcrack的明文爆破
1 | |
1 | |
1 | |
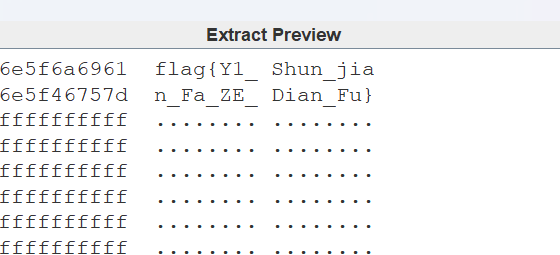
steg看一下
ai
backdoor
1 | |
春秋杯冬季赛2025
https://0ran9ewww.github.io/2025/01/19/春秋杯/春秋杯冬季赛2025/