第八届强网拟态决赛-Misc
本文最后更新于 2025年11月30日 下午
Misc
泄漏的时间与电码(三血)
把log和chal的加密脚本直接扔给ai
1 | |
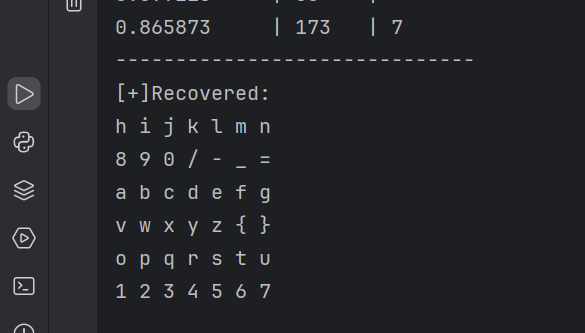
之后没思路无能狂怒了一天
官方hint的内容是ModR/M
已知给的chal的elf文件就说加密脚本直接在linux环境编译的,尝试反编译未找到可利用的内容,利用ai检索信息ModR/M,问了隐写得到了一个项目
woodruffw/steg86: Hiding messages in x86 programs using semantic duals
猜测可能是,装一下环境
得到了这个内容,把密文和字符表扔个ai
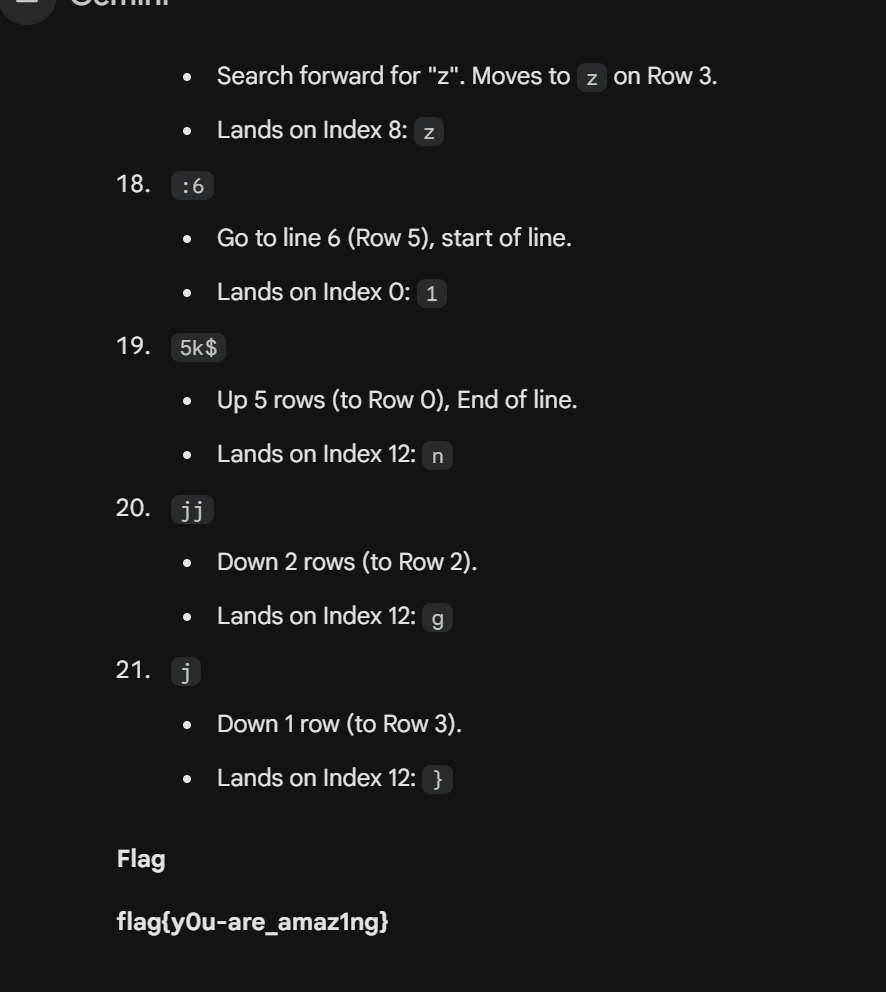
Vim 编辑器进行宏操作验证的一个题目
标准的绝密压缩(三血)
题目给了一个流量包,
简单的tcp分析发现是有png的hex流的
1 | |
然后提取出所有的图片
1 | |
提取出来发现是1kb规则的图片,看不出任何名堂,于是放弃(中途三个小时去看了其他的)
最终还是回归png的,尝试了
1 | |
30张图片都是有问题的,且都是可打印字符,那么就是朝着png想,翻了翻lunatic师傅的博客,检索到了可能是idat隐写,手动调整一下
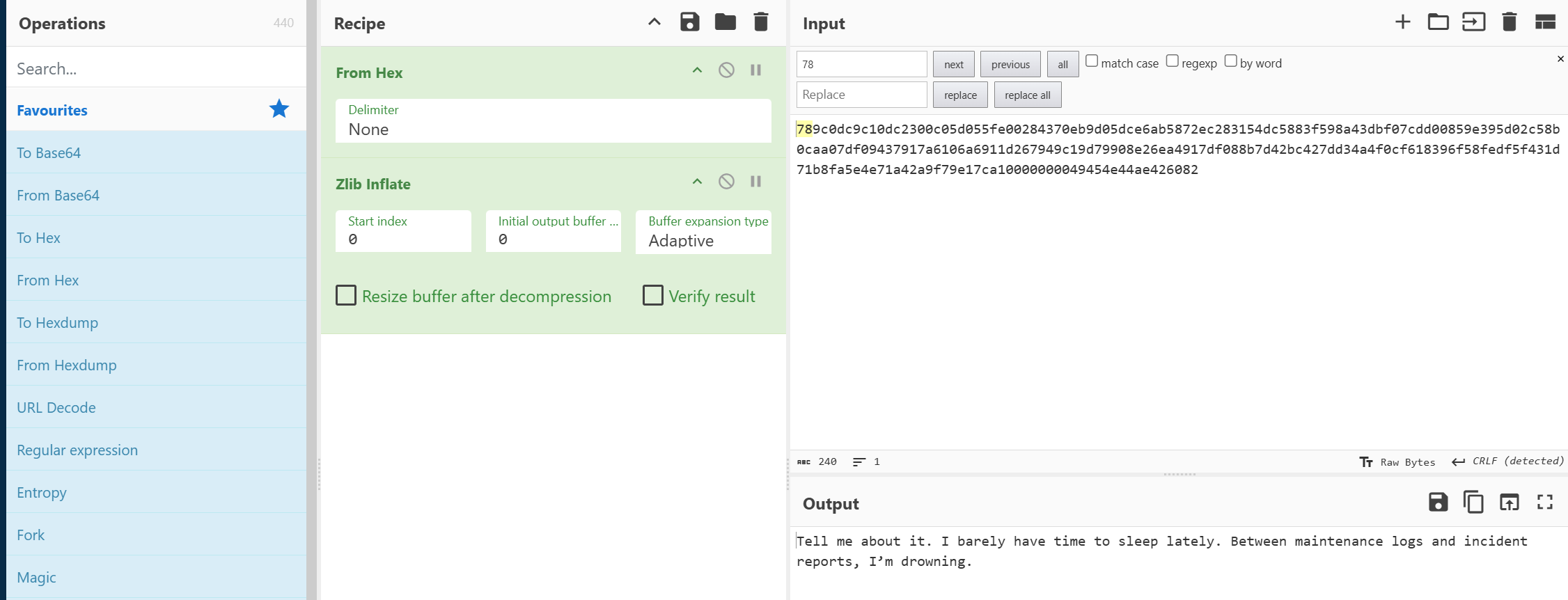
超绝震撼,把30条信息都提取出来,最后的信息是
1 | |
中间的解码可以拿到压缩包
一眼明文攻击,这里回归文本
1 | |
那么sample.txt就是需要社工的地方,找到对应文本内容
Him.Html | Minecraft CreepyPasta Wiki | Fandom
这里就是拷打ai进行网页社工找到了对应内容
1 | |
文件大小略有出路,最终的内容是
1 | |
这里利用7z制作压缩包
利用ARCHPR进行攻击解压同时得到密钥
1 | |
rule文本的内容是
1 | |
然后又陷入了深思
大致的思路利用对应的端口的MD5作为key解密内容
1 | |
仔细分析一下内容(这里有点脑王争霸),发现端口30012-30091之间的区别与前面png传输的内容,拼接起来是乱码,尝试发现是AES加密
那么就可以写个脚本提取出所有的压缩包了
1 | |
得到对应的压缩包,这里仔细分析压缩包里的内容是4字节,应该是CRC爆破,有不可见字符参考lunatic师傅的脚本
1 | |
然后根据一开始的提示deflated了,那么我们inflate一下,搓个脚本得到了
1 | |
得到了一个hash的值
分析一下hash,算是zipCrypto的特性,里面文本内容较短,在进行hash转储的时候会将内容全部放入到hash中进行加密,从开始的文本聊天得知,这边的密钥可以进行复用,在已知hash和key后可以hash反推压缩包得到flag的内容,脚本如下
1 | |
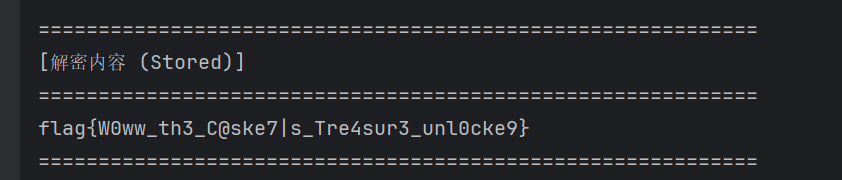
返璞归真(一血)
给的压缩包开头有提示hashisk3y
这里直接伪加密解压得到图片,利用foremost进行分离得到dmp,利用项目
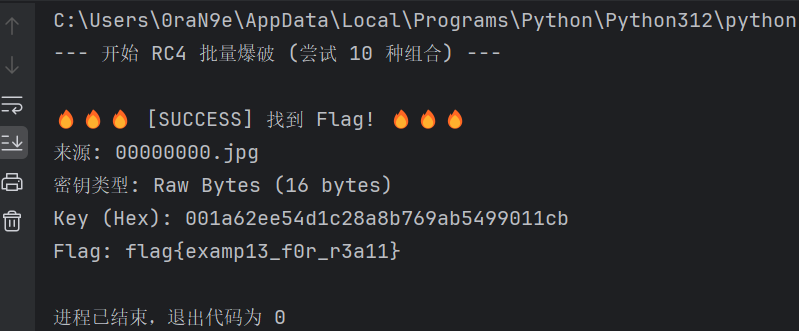
进行分离拿到文本内容,这里是23字节,卡了一会,最后是猜测是RC4,将可能的hash值都运行下来,直接扔个ai分析得到flag
1 | |
猫咪电台(一血)
题目给了一个图片和一个wav
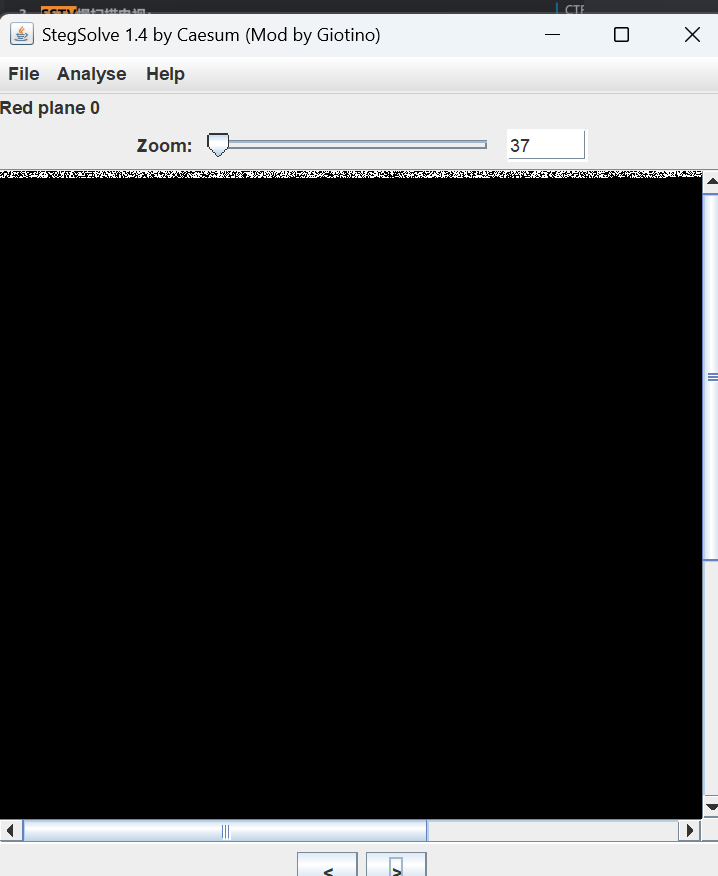
图片里面应该有东西,分析一下lsb隐写,提取出来
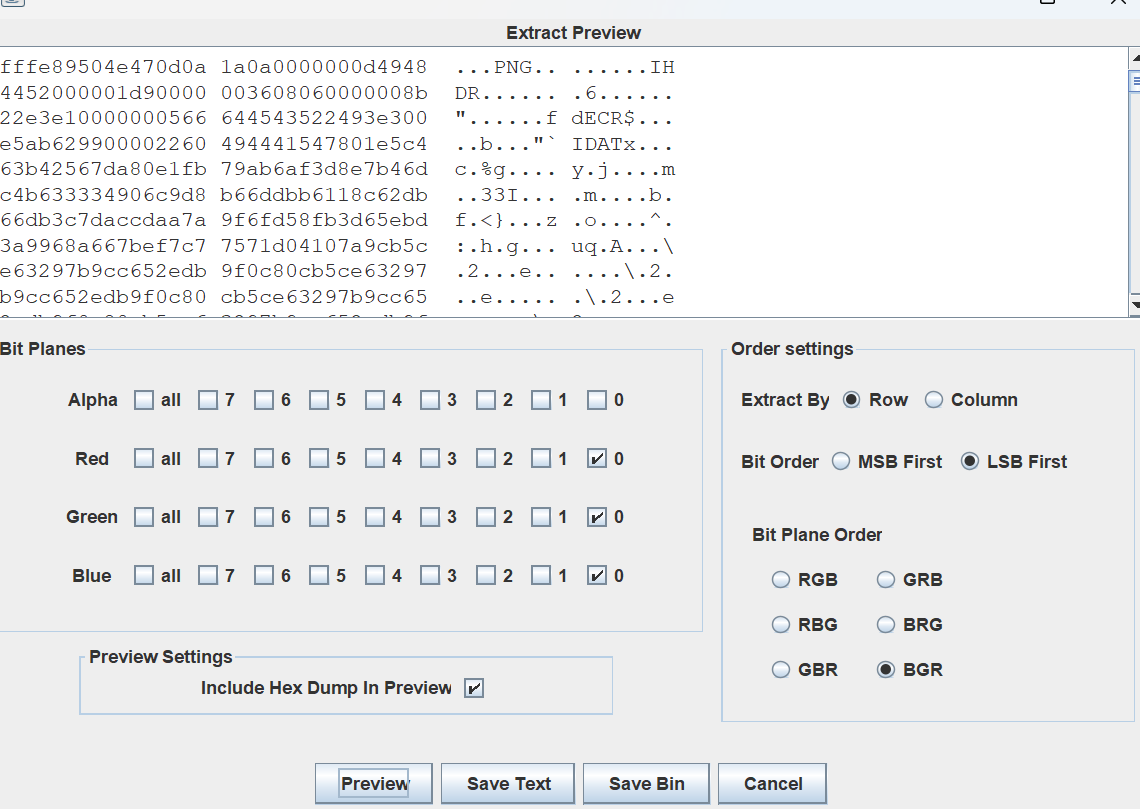
去掉开头fffe得到图片
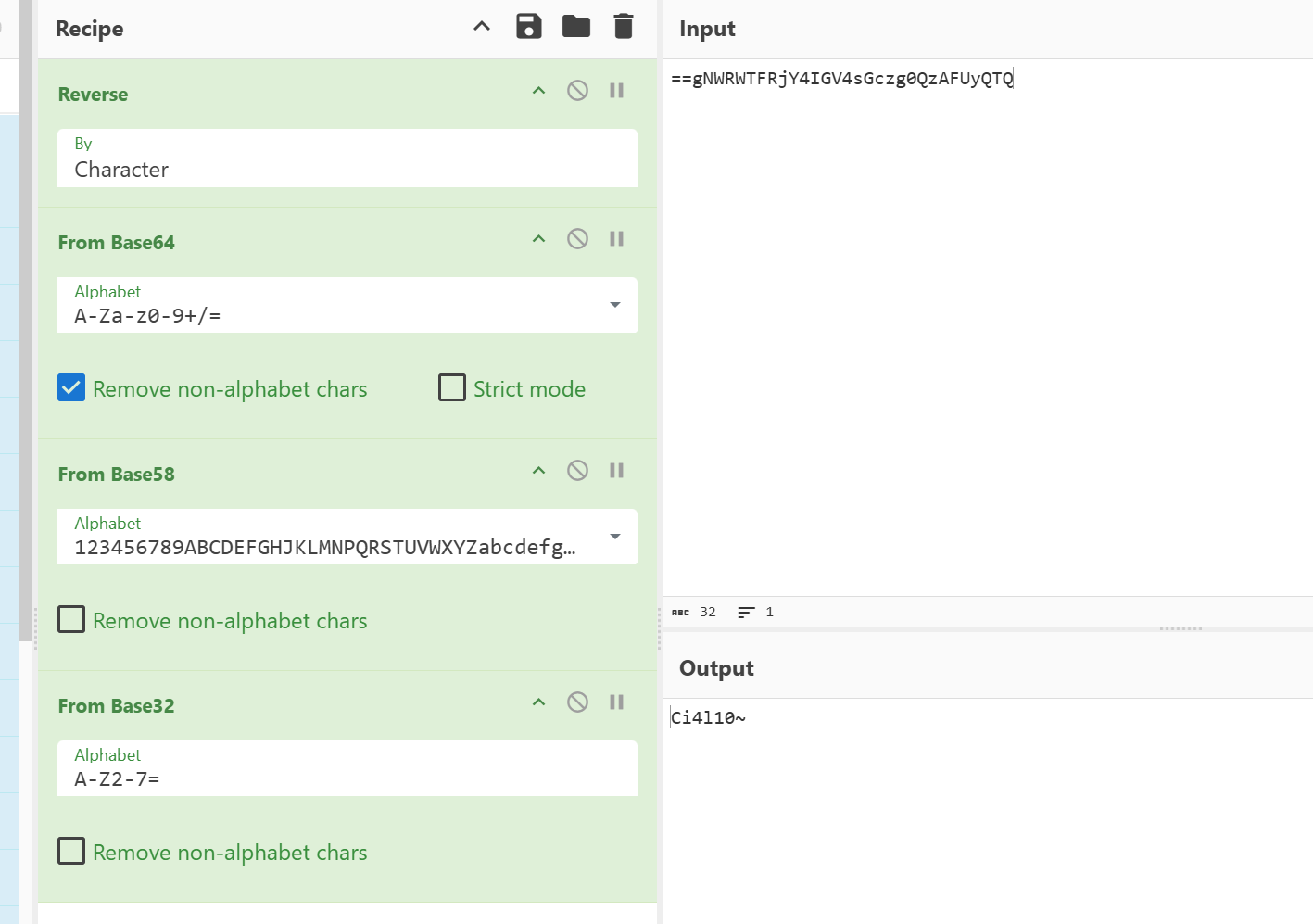
wav用010分析后面有一个巨大的压缩包,分离出来。
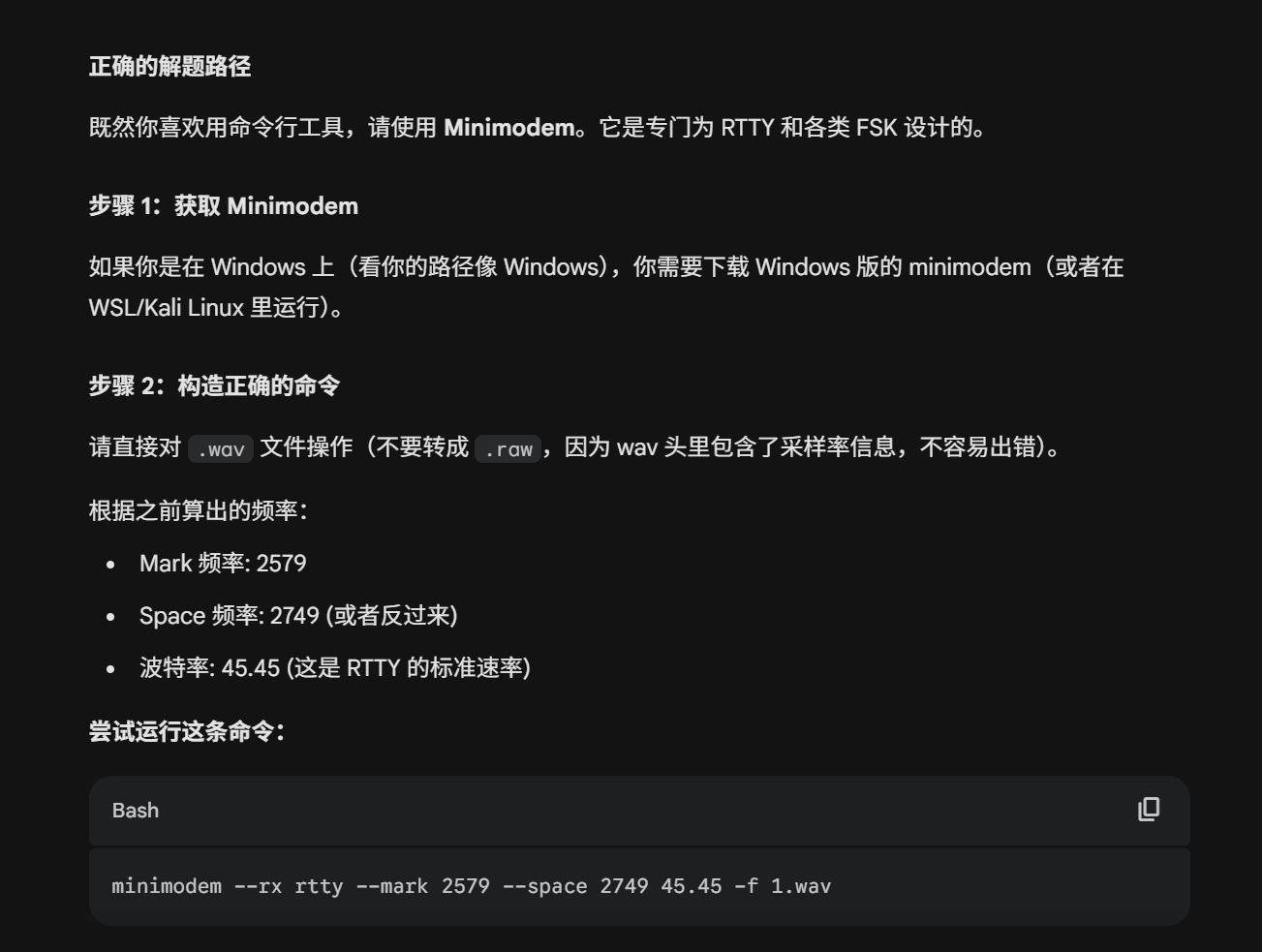
根据文件夹的提示,以及尝试发现1.wav不是sstv后联想到是无线电的音频
问ai有哪些工具可以进行尝试
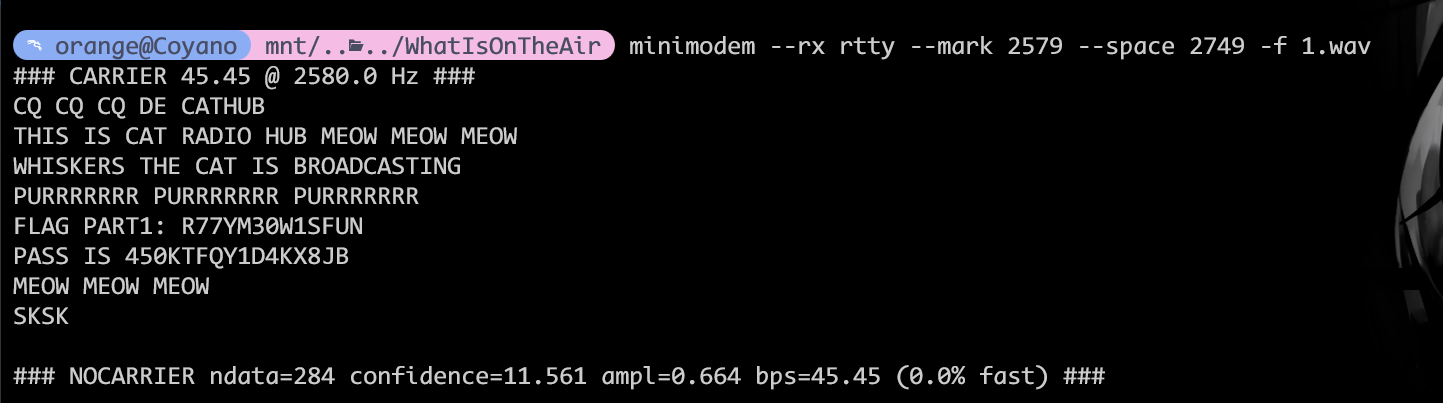
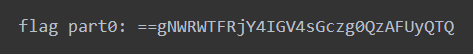
得到了part1 R77YM30W1SFUN
这个密码可以解压得到2.wav
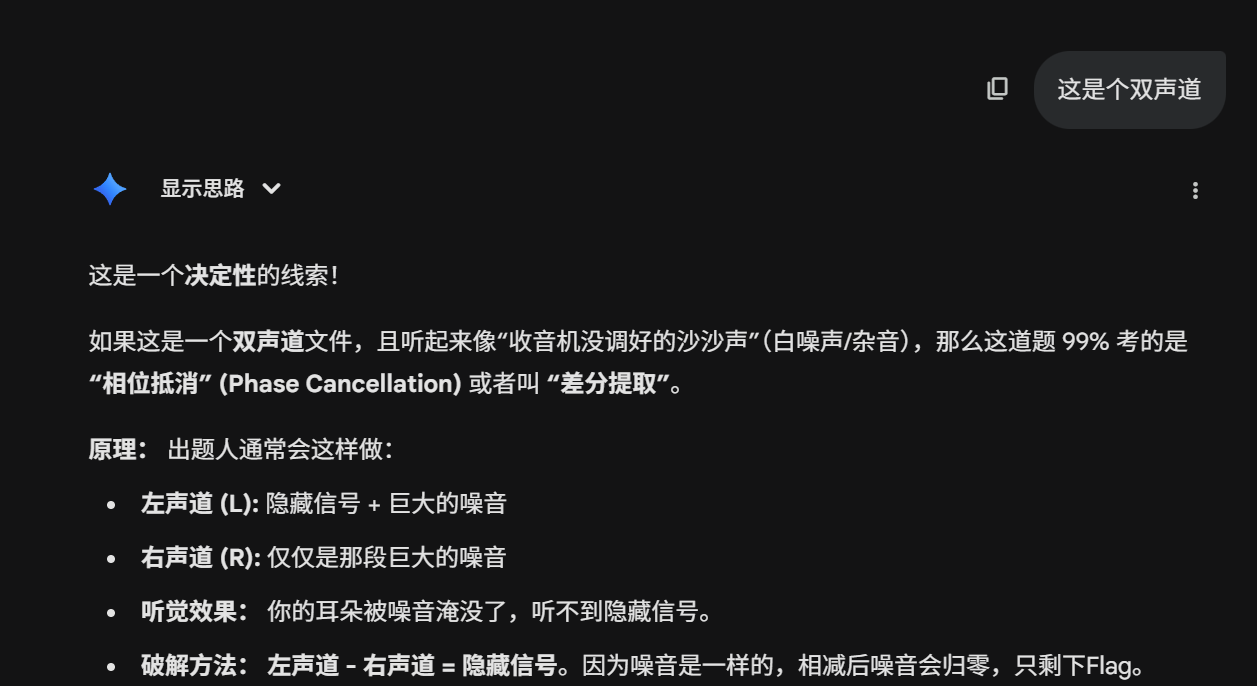
2.wav是个很杂的音,双声道
1 | |
但还是杂音
回头看了一下文件的hz
1 | |
跑出个脚本
1 | |
发现中间是有类似sstv的东西的,用工具跑看看
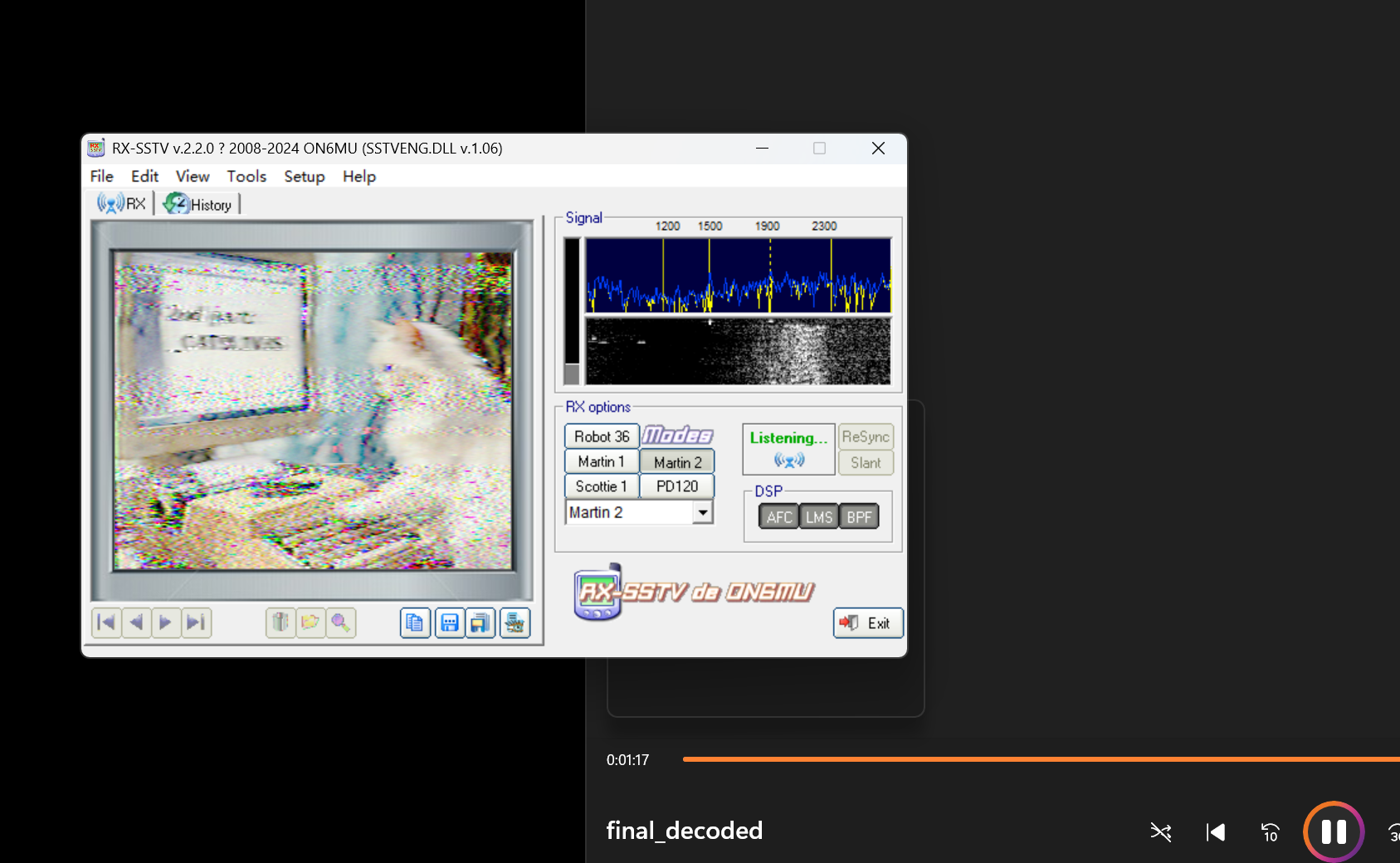
是图片不过需要去噪啊
然后写了一个稍微能看到一点的
1 | |

出的时候试了好几次,最后应该是2nd part _C4T9L1V3S
1 | |
后话
赛中还研学了一下web层层加码,n4cl师傅payload一穿三太强了,可惜3.2过于恶心。
主办方过于富裕,线下比赛体感最好的一集,和很多SU的伙伴见面约饭了。这里还是宣传一波,欢迎各位有意加入战队的师傅们投递简历到SUsu-team。战队采用的是candidate过渡考察的机制,进入我们的Discord打几周之后考察转正(问了一下处在candidate的师傅们起初觉得我们可能审核比较严,闹大误会了),祝SU全年起飞,偶尔摸鱼。